User application hardening protects an organisation from a range of threats including malicious websites, advertisements running malicious scripts and exploitation of vulnerabilities in unsupported software. These attacks often take legitimate application functionality and use it for malicious purposes. User application hardening makes it harder for cybercriminals to exploit vulnerabilities or at-risk functionality in your organisation’s applications.
Before you begin
Review the Small business cloud security guides introduction before you use this technical example. The introduction includes steps you should take before you begin, including:
- Check that you have a compatible Microsoft 365 subscription. This technical example requires a subscription to Microsoft 365 Business Premium (or equivalent).
- Enable security defaults in Azure Active Directory. Microsoft has published guidance on enabling Security defaults.
- Enrol your compatible devices in Intune. Microsoft has published guidance on enrolling Windows devices in Intune.
The steps taken in this technical example require an account with 'Intune Administrator' or 'Global Administrator' privileges.
Why you should harden user applications
User application hardening protects an organisation from a range of threats including malicious websites, advertisements running malicious scripts and exploitation of vulnerabilities in unsupported software. These attacks often take legitimate application functionality and use it for malicious purposes. User application hardening makes it harder for cybercriminals to exploit vulnerabilities or at-risk functionality in your organisation’s applications. It limits the opportunities for attacks to occur by removing unnecessary system applications and placing restrictions on application functions that are vulnerable to malicious use. Hardening applications on workstations is an important part of reducing your organisation’s cybersecurity risk.
Requirements for user application hardening
This technical example is adapted from Essential Eight maturity level one. It is designed to meet the following requirements:
- Web browsers do not process Java from the internet.
- Web browsers do not process web advertisements from the internet.
- Internet Explorer does not process content from the internet.
- Web browser security settings cannot be changed by the users.
What this technical example covers
This technical example demonstrates one way to implement user application hardening for Microsoft 365 applications, also covering the Google Chrome web browser. It uses Microsoft’s security defaults as well as web browser settings that are configured through Microsoft Intune. This technical example does not cover applications that are outside of the Microsoft 365 ecosystem. Any other applications your organisation uses should be hardened in accordance with the application’s vendor guidance.
Technical example
Note: This technical example builds upon Microsoft’s security defaults and deploys hardened applications with Microsoft Intune. Ensure you have followed the guidance in the ‘Before you begin’ section on enrolling your organisation’s devices in Intune and enabling security defaults.
1. Log into the Microsoft Intune admin center. Select Devices in the main menu then select Configuration profiles. Select Create profile from the menu items at the top of the page.
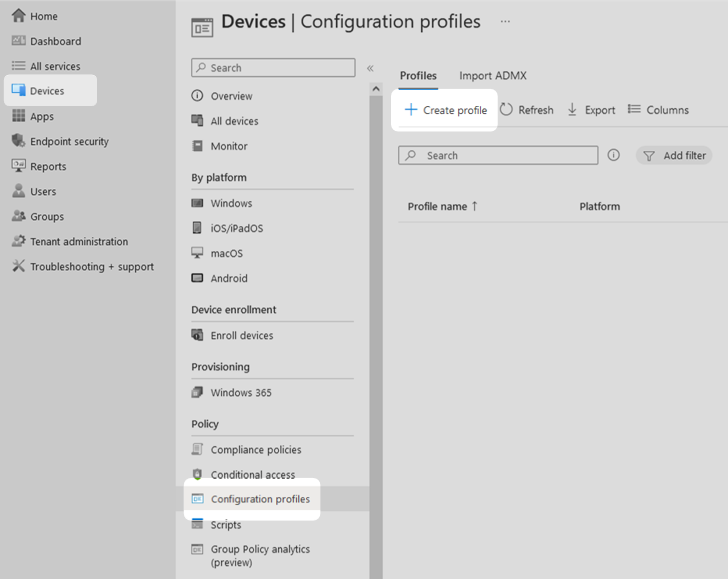
2. On the Create a profile panel, select the platform that your organisation uses, this technical example uses Windows 10 and later. Select the profile type Settings catalogue, then select Create.
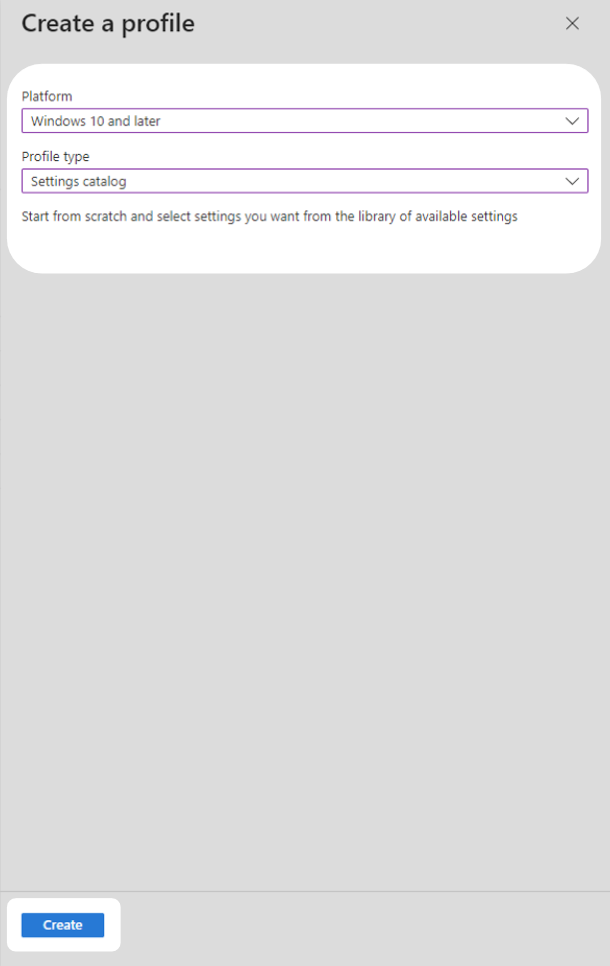
3. In the Basics windows, select a profile name and description then select Next.
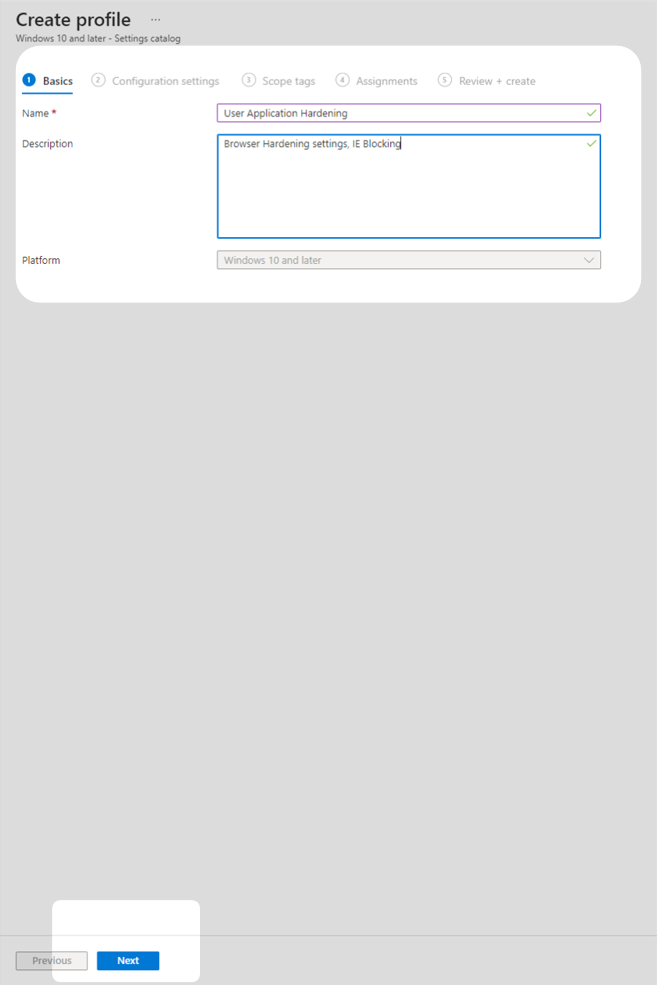
Edge and Chrome Settings
4. In Settings picker, select Microsoft Edge then Ads settings for sites with intrusive ads. Under the Microsoft Edge heading in the middle pane, select Enabled and ensure Block ads on sites with intrusive ads. (Default value) is also toggled on.
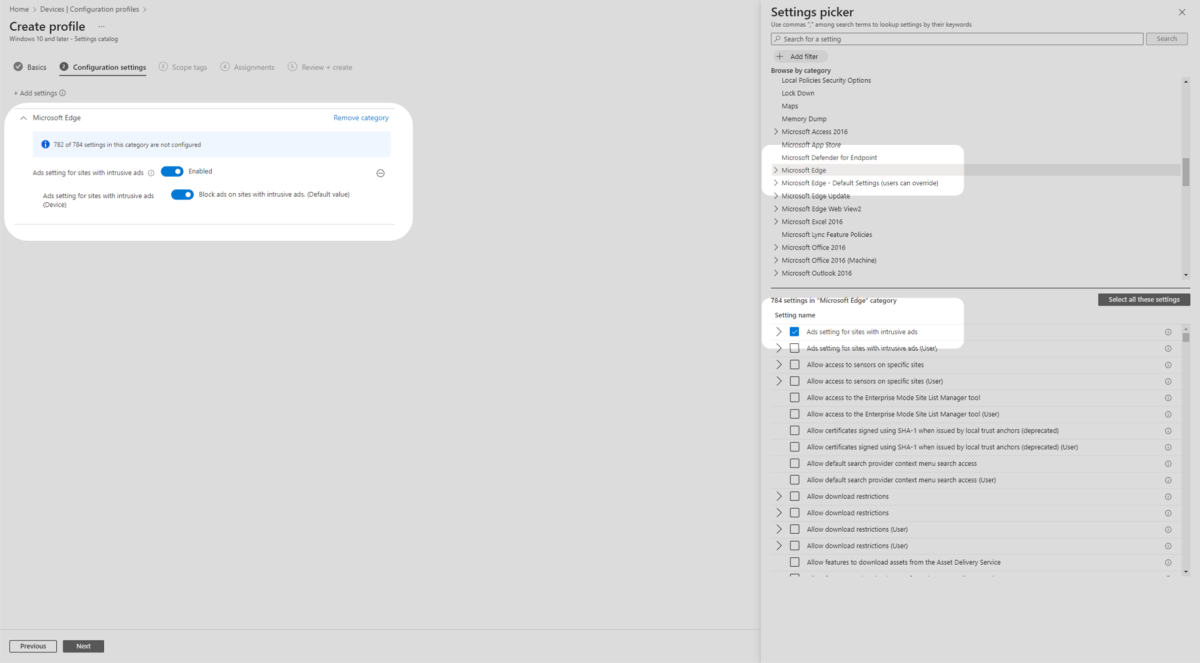
5. Then, under Microsoft Edge in the Settings picker pane, select Extensions and select Blocks external extensions from being installed. Then ensure Blocks external extensions from being installed is toggled on in the middle pane.
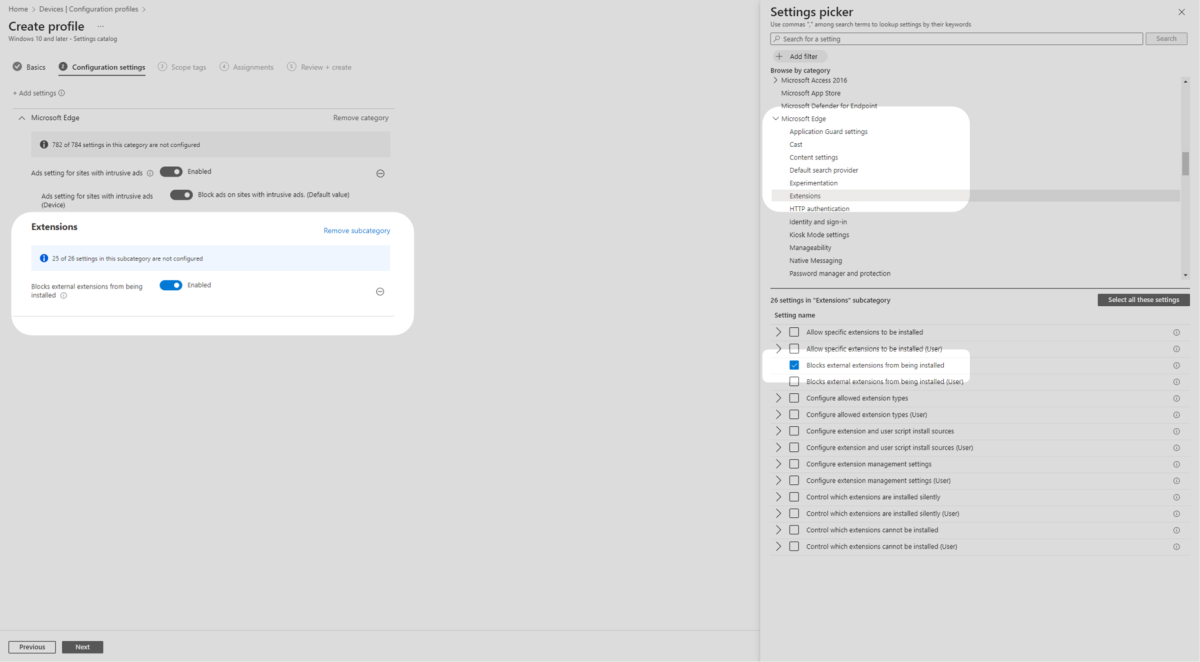
6. Ensure Microsoft Edge is still selected in Settings picker. Then select Smart Screen Settings. Then tick the following options:
- Configure Microsoft Defender SmartScreen
- Configure Microsoft Defender SmartScreen to block potentially unwanted apps
- Prevent bypassing Microsoft Defender SmartScreen prompts for sites
- Prevent bypassing of Microsoft Defender SmartScreen warnings about downloads.
Ensure that you have enabled all the SmartSceeen settings by toggling them on.
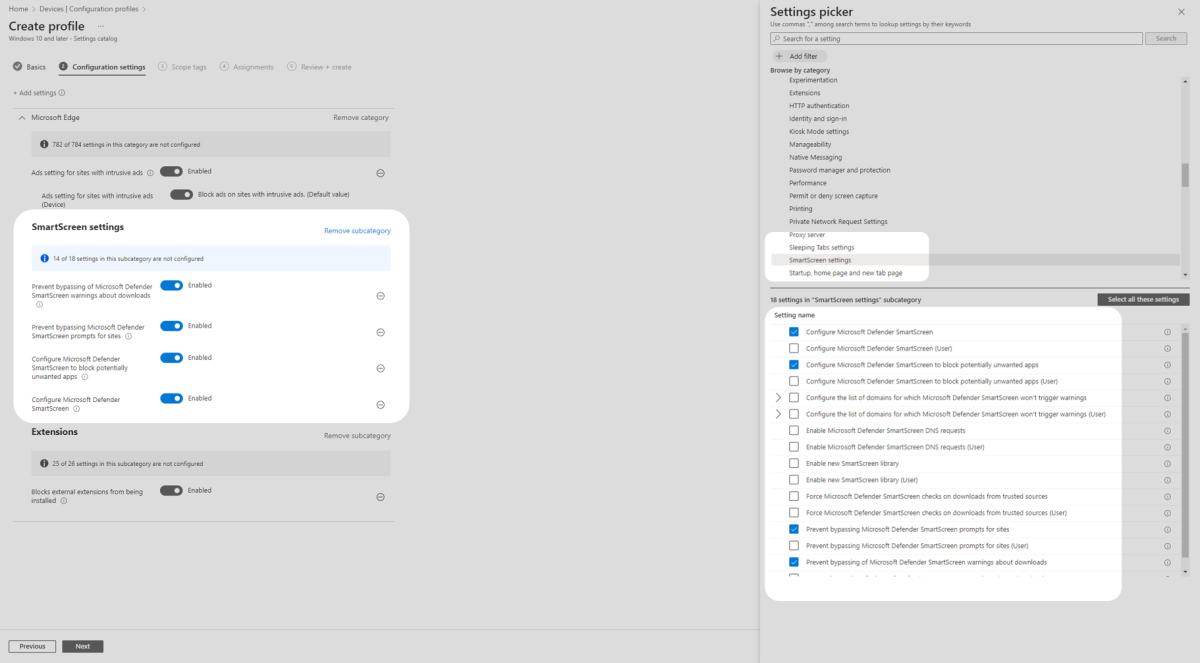
7. Select Administrative Templates, then select Google Chrome. In the Settings picker pane, select Ads setting for sites with intrusive ads. Then in middle pane toggle both Ads setting for sites with intrusive ads and Do not allow ads on sites with intrusive ads are toggled on.
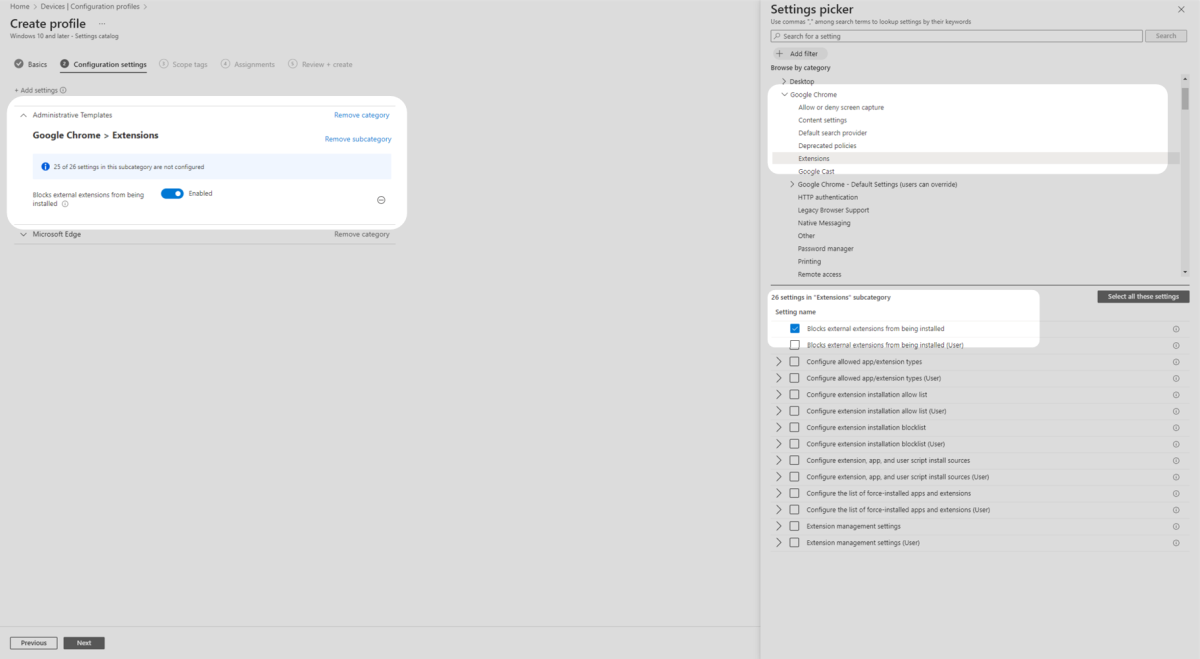
8. Ensure you are still in Administrative Templates and Google Chrome in the Settings picker. Select Extensions and check Blocks external extensions from being installed. Then ensure it is toggled on in the middle pane. Note extensions from the Chrome App Store are still available.
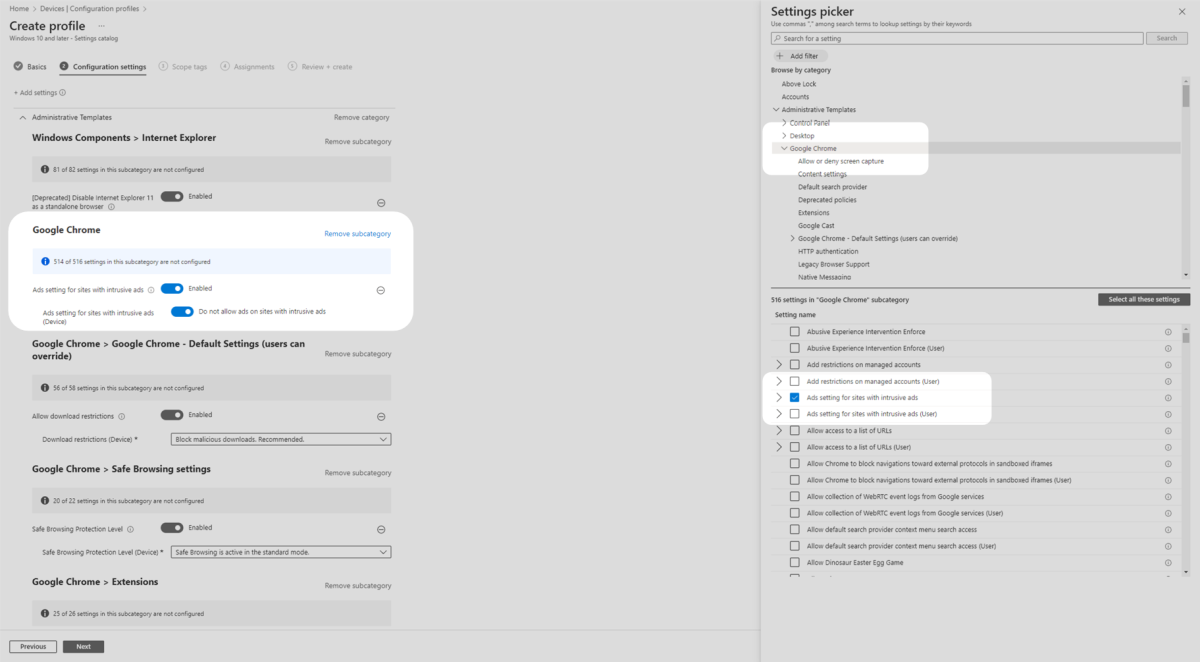
9. Ensure you are still in Administrative Templates and Google Chrome in the Settings picker. From the middle pane, select Safe Browsing Protection level. Ensure it is Enabled. Then select Safe Browsing is active in the standard mode from the drop down menu.
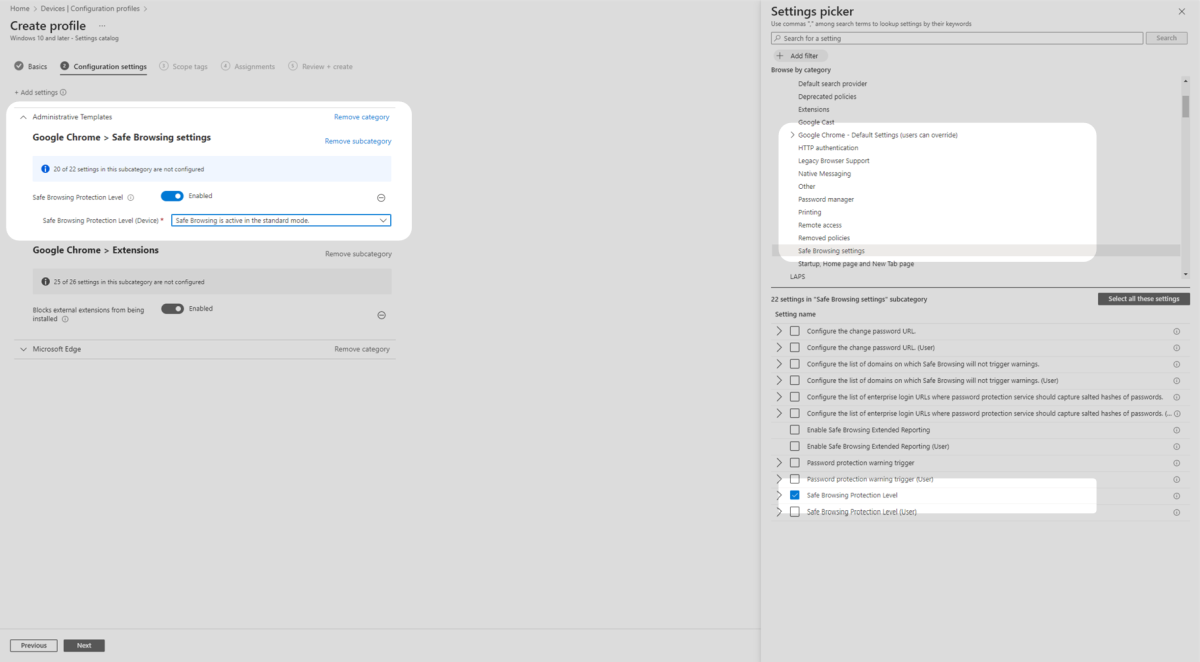
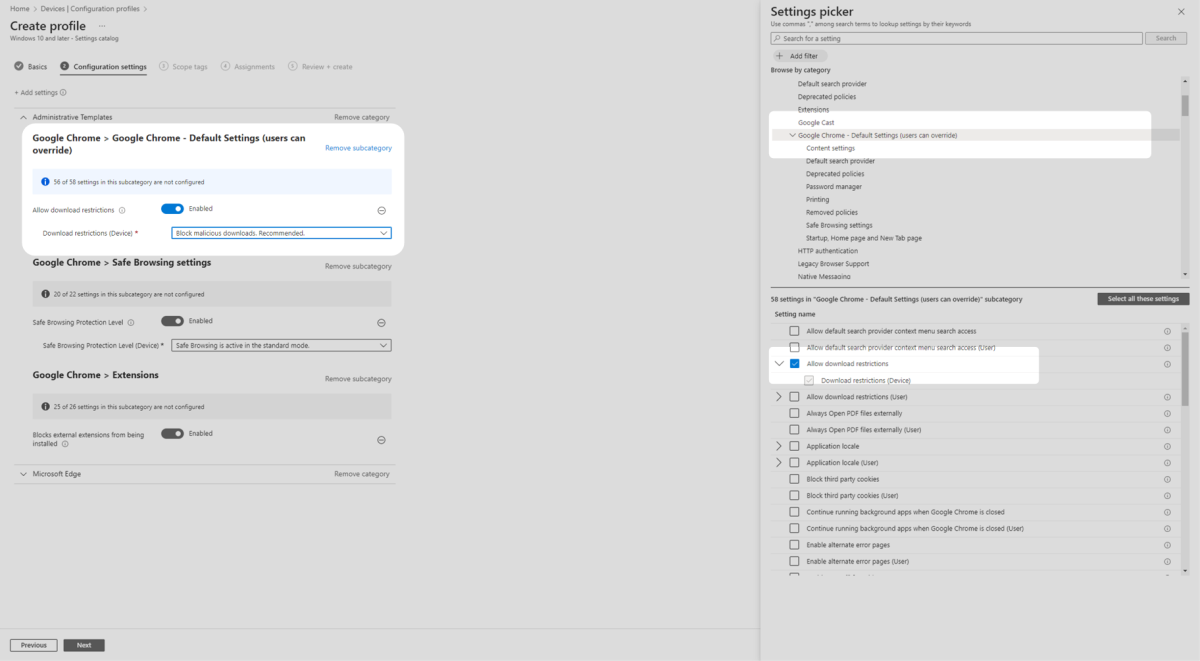
10. Then select Google Chrome – Default Settings (users can override) then select Allow download restrictions. Ensure it is toggled on in the middle pane and then set Block malicious downloads to Enabled. (Continue on step 11)
Internet Explorer 11 does not process content from the internet
As of 15 June 2022, Internet Explorer 11 has officially reached end-of-life and is no longer supported by Microsoft. Microsoft has outlined a two phased retirement approach, beginning with ‘Redirection’ and ending with the ‘Update’ phase.
11. Select Administrative Templates, then select Windows Components then Internet Explorer. Then select [Deprecated] Disable Internet Explorer 11. Ensure the setting is toggled on in the middle pane.
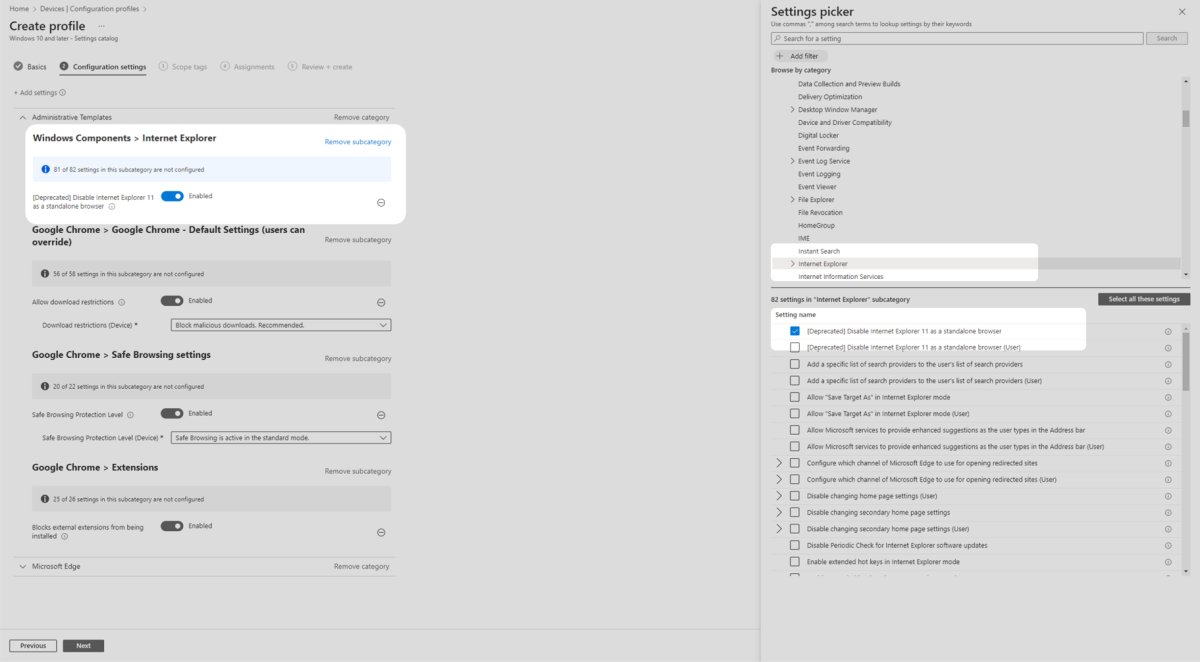
Note: This setting is deprecated and Microsoft has indicated that the February 2023 update of Windows will remove Internet Explorer 11.
If your organisation requires Internet Explorer 11, for example to access legacy intranet pages, it is best practice to use ‘IE Mode’ in Microsoft Edge with a vetted local site list enabled.
Finalise configuration profile
12. After configuring the settings above, select Next.
13. You will be given an opportunity to select scope tags. This technical example progressed with the default settings for this step. Your organisation should configure scope tags according to its needs then select Next.
14. Assign the configuration profile to All devices then select Next.
15. Confirm that the configuration profile is setup as intended then select Create.
Web browsers do not process Java from the internet
All modern, up-to-date, web browsers have dropped support for Java plugins due to well documented security risks. The only web browser that still has support for the Java Applet is Internet Explorer 11. This technical example meets the requirement to prevent web browsers from processing Java from the internet by disabling Internet Explorer 11 and only using up-to-date web browsers.
Web browser security settings cannot be changed by the user
Security policies that are deployed in your environment via Intune, or when configured via group policy objects or mobile device management, are enforced by the system and cannot be changed by standard end user workstations. This technical example used the Setting Catalogue configuration profile type, this ensures that, once deployed, the policies become mandatory and cannot be changed by standard users. Microsoft has published additional advice on configuring Microsoft Edge policy settings.
Known limitations
Users may be able to install their own web browsers that do not have policies enforced from Microsoft Intune. Some web browsers may not have built-in security functions.
The use of web advertisement blocking functionality reduces the opportunity for malicious scripts to run through web advertising however no solution is guaranteed to be completely effective.
