Patching operating systems is one of the most effective controls an organisation can implement to prevent an adversary from gaining access to their devices and sensitive information. Patches improve the security of operating systems by fixing known vulnerabilities.
Before you begin
Review the Small business cloud security guides introduction before you use this technical example. The introduction includes steps you should take before you begin, including:
- Check that you have a compatible Microsoft 365 subscription. This technical example requires a subscription to Microsoft 365 Business Premium (or equivalent). A limited number of administrators will require an Azure Active Directory Premium P2 licence (or higher) to use Microsoft’s Privileged Identity Management functionality.
- Enable security defaults in Azure Active Directory. Microsoft has published guidance on enabling Security defaults.
- Enrol your compatible devices in Intune. Microsoft has published guidance on enrolling Windows devices in Intune.
The steps taken in this technical example require an account with Privileged Role Administrator or Global Administrator privileges.
Why you should implement operating system patching controls
Patching operating systems is one of the most effective controls an organisation can implement to prevent an adversary from gaining access to their devices and sensitive information. Patches improve the security of operating systems by fixing known vulnerabilities. Cyber criminals exploit vulnerabilities as soon as they are publicly disclosed so organisations should patch their applications as a priority.
Cyber criminals scan internet-facing services with automated tools that gather information about potentially vulnerable systems. This information can be used by cyber-criminals to target at-risk businesses. Regular vulnerability scanning can identify gaps in your organisation’s attack surface that require patching.
Requirements for operating system patching
This technical example is adapted from Essential Eight maturity level one. It is designed to meet the following requirements:
- Patches, updates or vendor mitigations for security vulnerabilities in operating systems of internet-facing services are applied within two weeks of release, or within 48 hours if an exploit exists.
- Patches, updates or vendor mitigations for security vulnerabilities in operating systems of workstations, servers and network devices are applied within one month of release.
- A vulnerability scanner is used at least daily to identify missing patches for security vulnerabilities in operating systems of internet-facing services.
- A vulnerability scanner is used at least fortnightly to identify missing patches for security vulnerabilities in operating systems of workstations, servers and network devices.
- Operating systems that are no longer supported by vendors are replaced.
What this technical example covers
This technical example demonstrates one way to configure Windows to automatically update the operating system of enrolled Windows 10 or Windows 11 devices. The technical example configures settings to update devices within a deadline using an Update ring policy in Microsoft Intune. Organisations that are using other operating systems with Microsoft 365 will need to consider how to keep those systems appropriately updated. Tenant administrators should still periodically check update compliance to ensure systems are kept up to date.
There are two types of Windows updates: feature updates and quality updates. Feature updates are available once a year and provide new features to Windows. Quality updates are incremental and are intended to provide security fixes to protect systems running Windows. This technical example is focused on quality updates.
Technical example
Automatically updating Windows
Note: This technical example assumes that devices are enrolled in Microsoft Intune.
1. Log into the Microsoft Intune admin center. Select Devices in the main menu then select Update rings for Windows 10 and later.
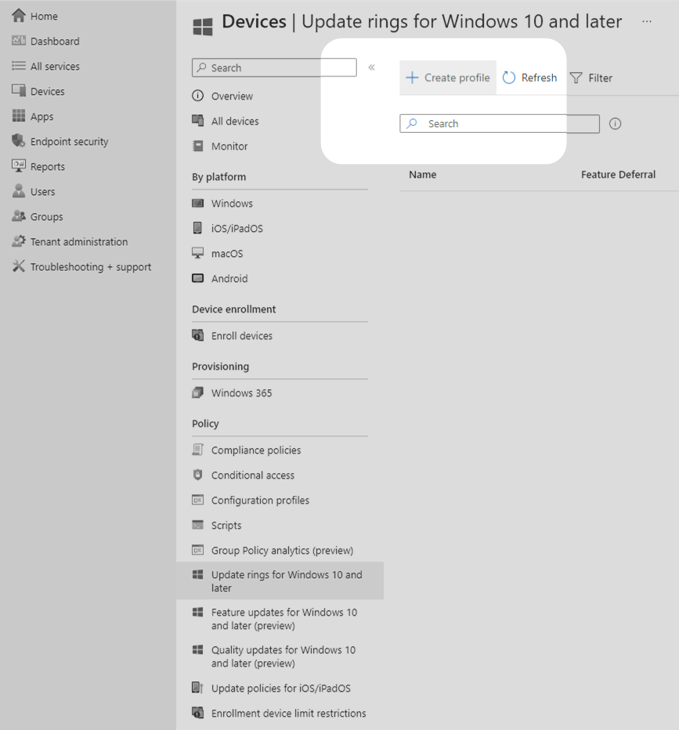
2. In the new centre window pane, select Create profile to create a new update policy for Windows deployments.
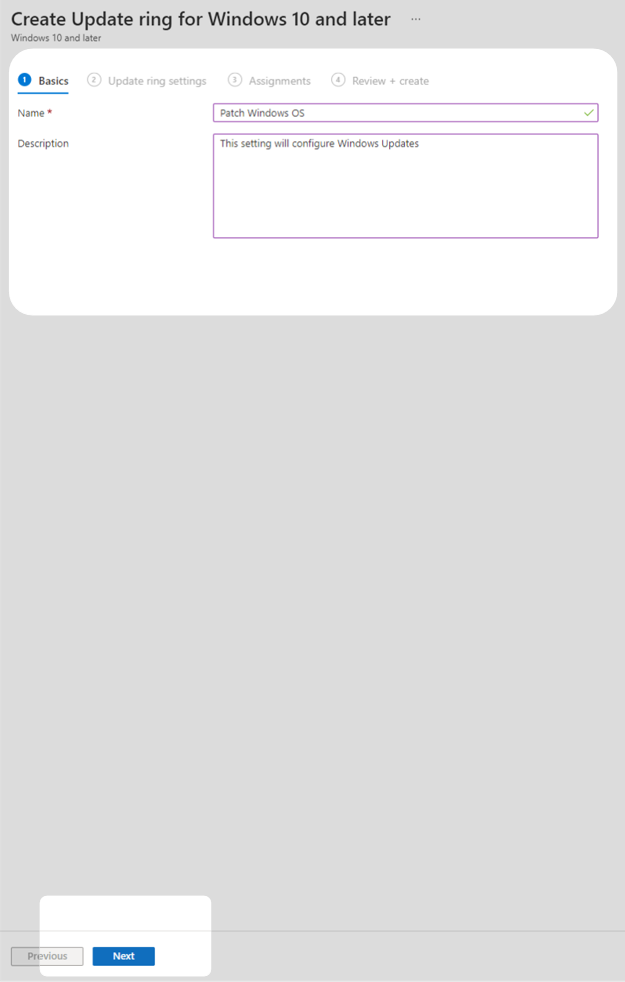
3. Provide a name and description then select Next.
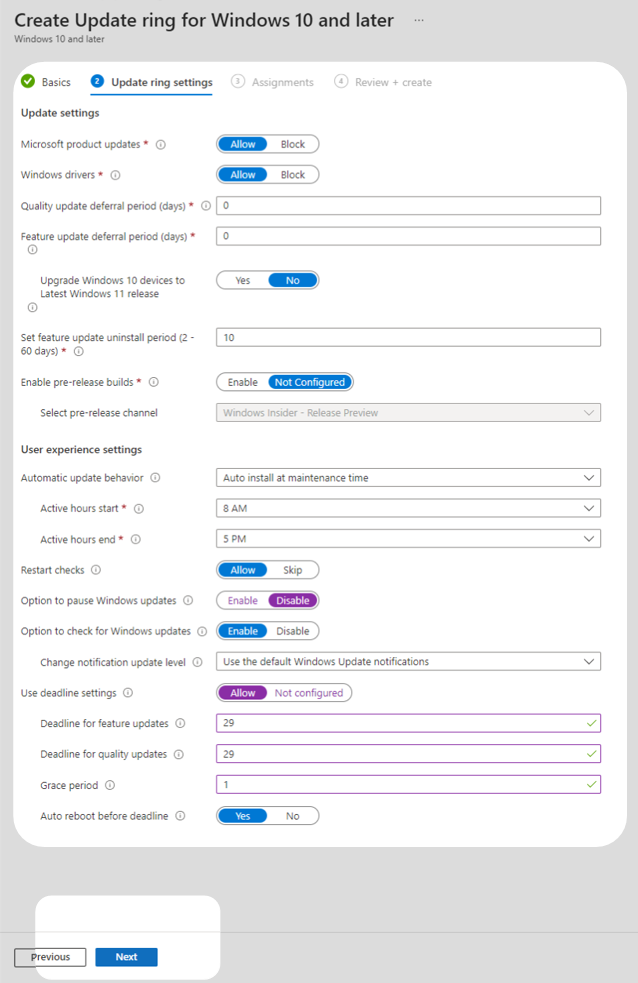
4. The Update ring settings tab provides several configuration options. The configuration chosen in this technical example is outlined below. Your organisation may need to change these settings according to its requirements.
a. Set the deferral period for quality and feature updates to the default of zero days, allowing users to install updates on day one.
b. Disable the option for users to pause Windows updates, preventing users from keeping an out-of-date version for longer than the configured deadline.
c. Enable deadline settings for quality updates with a 29 day deadline and a 1 day grace period, allowing users who have not updated by the deadline to find a minimally disruptive time to reboot.
d. Change the default active hours to best align with the standard working hours of staff.
e. Configure a deadline for feature updates based on business need.
All other settings can be left as default values. After configuring these settings, select Next.
Note: The update deadline is the time when the update is forcibly installed. The grace period is the time when a device is rebooted automatically after the installation of updates.
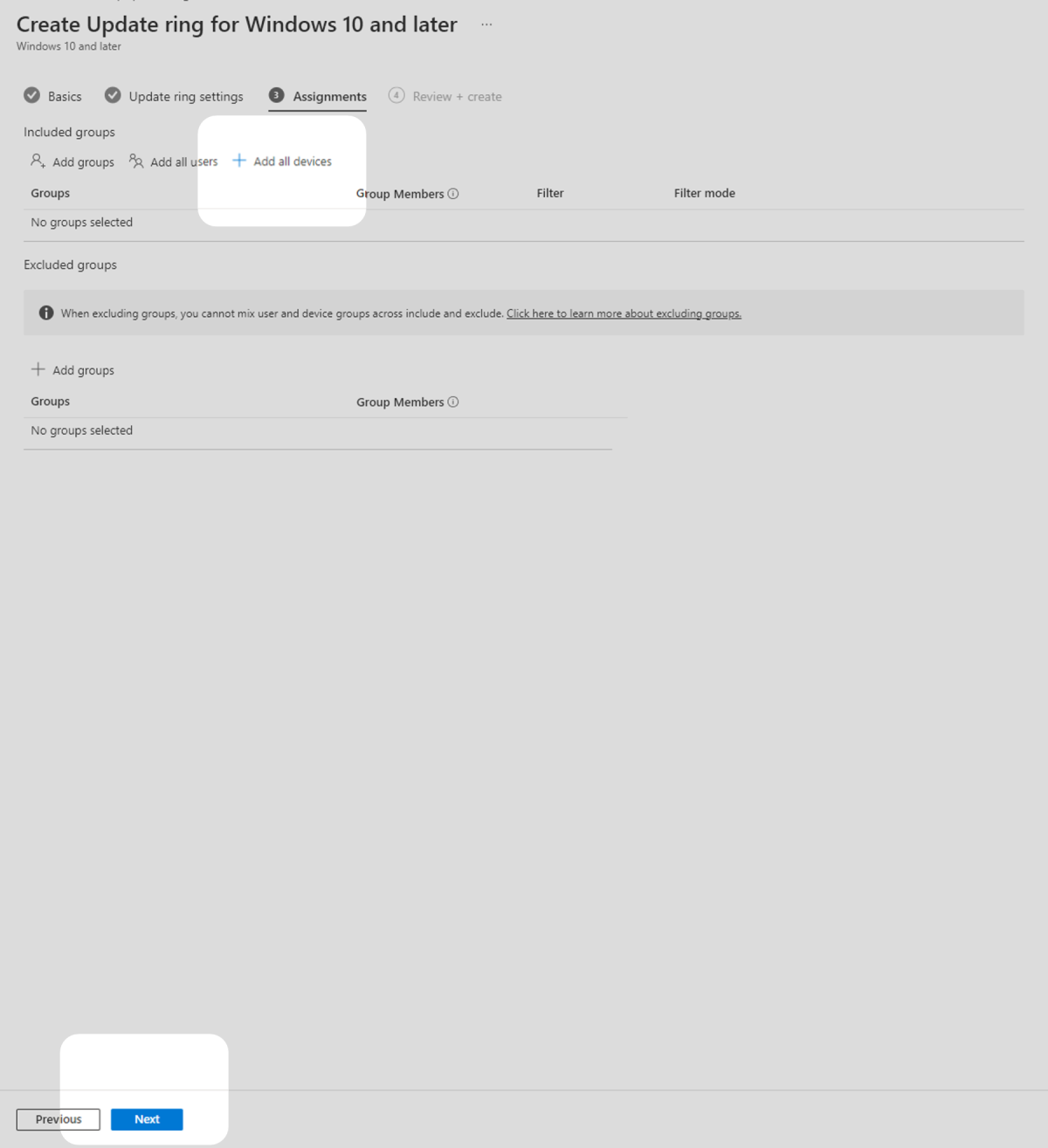
5. In the Assignments tab, select Add all devices under Required to deploy the policy to all enrolled devices then select Next.
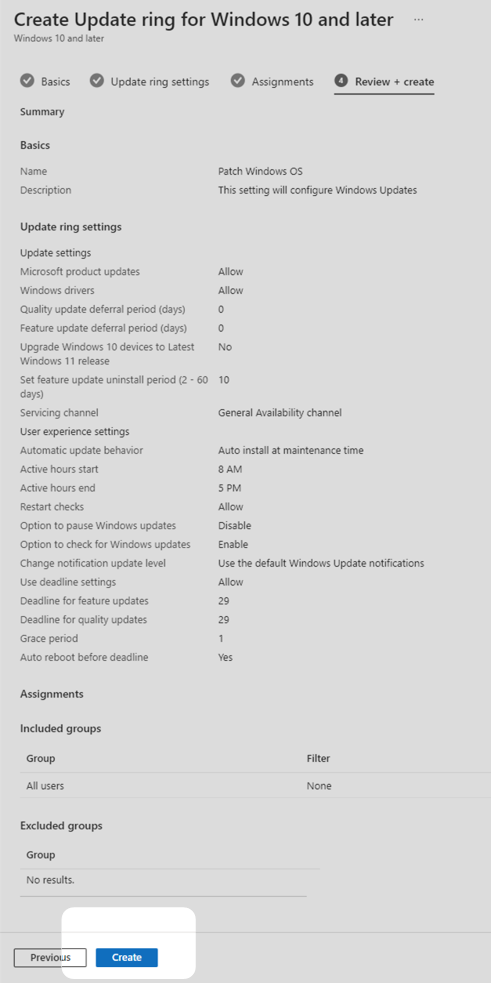
6. In the Review + create tab, confirm that your settings are correct then select Create to begin deployment of the policy.
Identify missing patches with a vulnerability scanner
This technical example uses Microsoft’s in-built vulnerability scanning to scan operating systems for internet-facing services.
Under normal operating conditions Microsoft’s Windows update tools will identify when Windows versions are out of date. Consider following existing Microsoft guidance to configure compliance reports for Windows updates and checking these reports regularly to ensure you are keeping operating systems up to date. If the above steps were followed, Windows updates will be applied in a timeframe that provides significant protection.
Remove unsupported products
It is up to IT staff to consider their organisation’s IT environment and determine if they are using operating systems that are not supported. For example, some Windows 10 releases and older versions of Windows may no longer be supported by Microsoft and should be removed in line with existing Microsoft guidance. If an unsupported operating system is required for a critical business function, IT staff should implement compensating security controls that sufficiently mitigate the risk, for example, ensuring any devices on the unsupported operating systems are unable to connect to other devices or the internet. More information on unsupported operating systems can be found in ASD's ACSC's End of Support for Microsoft Windows.
