Patching applications is one of the most effective controls an organisation can implement to prevent cyber criminals from gaining access to their devices and sensitive information. Patches improve the security of applications by fixing known vulnerabilities.
Before you begin
Review the Small business cloud security guides introduction before you use this technical example. The introduction includes steps you should take before you begin, including:
- Check that you have a compatible Microsoft 365 subscription. This technical example requires a subscription to Microsoft 365 Business Premium (or equivalent).
- Enable security defaults in Azure Active Directory. Microsoft has published guidance on enabling Security defaults.
- Enrol your compatible devices in Intune. Microsoft has published guidance on enrolling Windows devices in Intune.
The steps taken in this technical example require an account with Intune Administrator or Global Administrator privileges.
Why you should implement application patching controls
Patching applications is one of the most effective controls an organisation can implement to prevent cyber criminals from gaining access to their devices and sensitive information. Patches improve the security of applications by fixing known vulnerabilities. Cyber criminals exploit vulnerabilities as soon as they are publicly disclosed so organisations should patch their applications as a priority.
Cyber criminals scan internet-facing services with automated tools that gather information about potentially vulnerable systems. This information can be used by cyber-criminals to target at-risk businesses. Regular vulnerability scanning can identify gaps in your organisation’s attack surface that require patching.
Requirements for application patching
This technical example is adapted from Essential Eight maturity level one. It is designed to meet the following requirements:
- Patches, updates or vendor mitigations for security vulnerabilities in internet-facing services are applied within two weeks of release, or within 48 hours if an exploit exists.
- Patches, updates or vendor mitigations for security vulnerabilities in office productivity suites, web browsers and their extensions, email clients, PDF software, and security products are applied within one month of release.
- A vulnerability scanner is used at least daily to identify missing patches or updates for security vulnerabilities in internet-facing services.
- A vulnerability scanner is used at least fortnightly to identify missing patches or updates for security vulnerabilities in office productivity suites, web browsers and their extensions, email clients, PDF software, and security products.
- Internet-facing services, office productivity suites, web browsers and their extensions, email clients, PDF software, Adobe Flash Player, and security products that are no longer supported by vendors are removed.
What this technical example covers
This technical example demonstrates one way to configure automatic updates for Microsoft 365 applications. It applies to devices enrolled in Microsoft Intune that are running Windows 10 or Windows 11. This technical example does not cover applications that are outside of the Microsoft 365 ecosystem. Your organisation should implement controls that ensure any other applications it uses are also patched promptly, particularly any hosting services on the internet. Many applications will have their own mechanisms for regular patching. Guidance on patching should be available on the website of each application vendor.
Technical example
Ensuring applications are kept up-to-date
Note: This technical example deploys Microsoft 365 applications using Microsoft Intune. This allows IT staff to specify that updates and patches to Microsoft applications are applied automatically
1. Log into the Microsoft Intune admin center. Select Apps in the main menu then select All Apps. Select Add from the menu items at the top of the page.
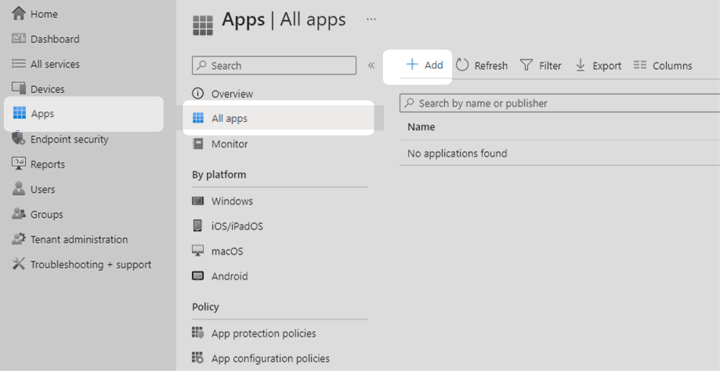
2. In the pane that appears, select the dropdown menu and select Windows 10 and later under Microsoft 365 Apps. Press Select at the bottom of the panel to continue to the next step.

3. Configure the app suite information according to your organisation’s needs then select Next. In this technical example, the default configuration was used.
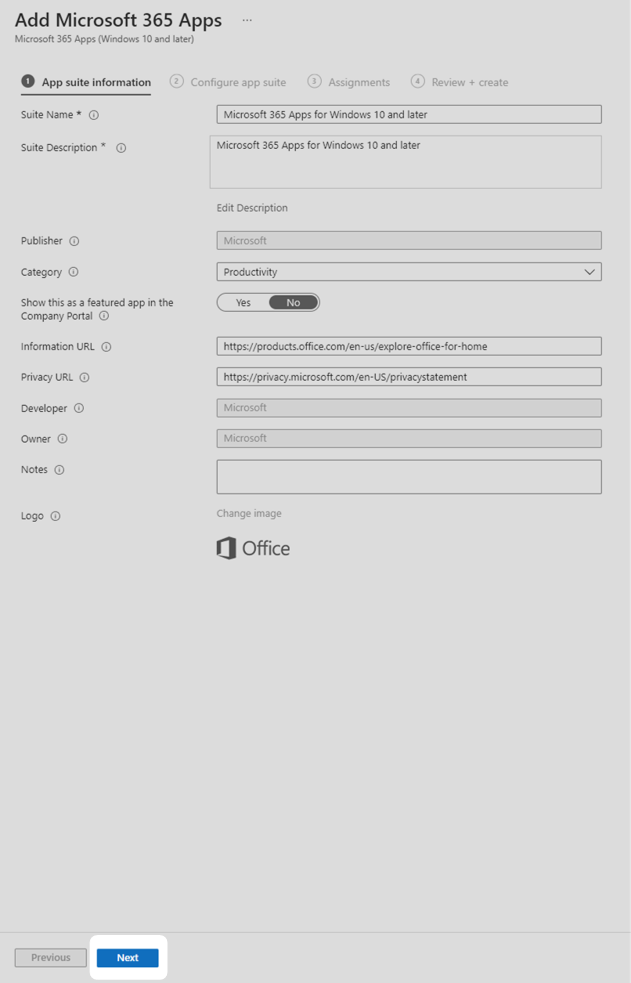
4. In the Configure app suite tab, select a default file format, select an Update channel, select Yes under Remove other versions and select Latest under version to install. In this technical example, ‘Current Channel’ was selected as the update channel, consult Microsoft’s overview of update channels to determine which channel is best for your organisation. On this screen you can also configure which Office apps need to be deployed. If you intend to have multiple user’s sharing a common computer, you should enable Use shared computer activation. Select Next.
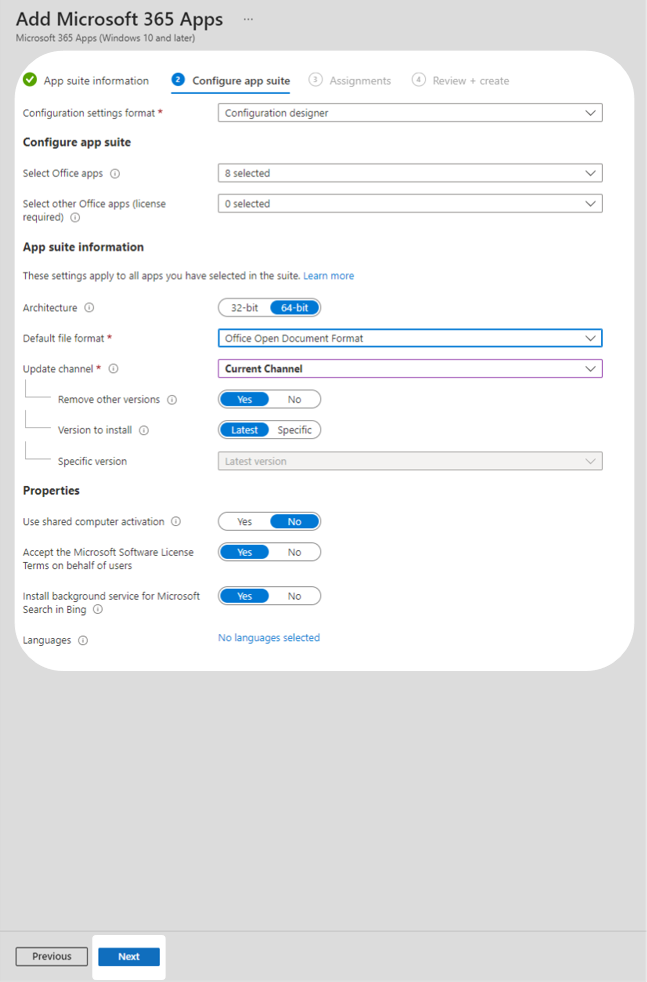
5. In the Assignments tab, press Add all devices to deploy Office applications to all enrolled devices. Select Next.
Note: This technical example deploys Office applications to all enrolled devices. Your organisation may prefer a different deployment strategy.
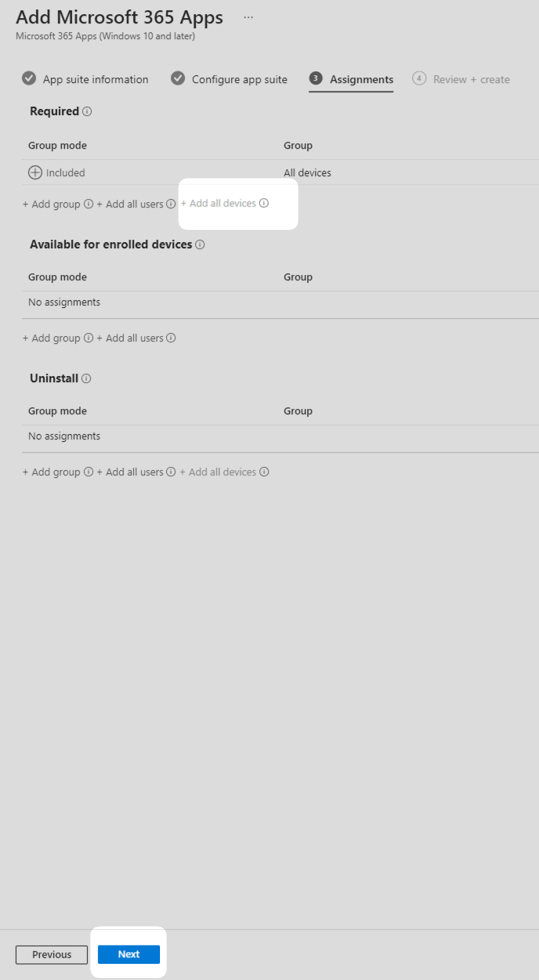
6. In the Review + create tab, ensure you are happy with your settings and press Create to begin deployment of apps.
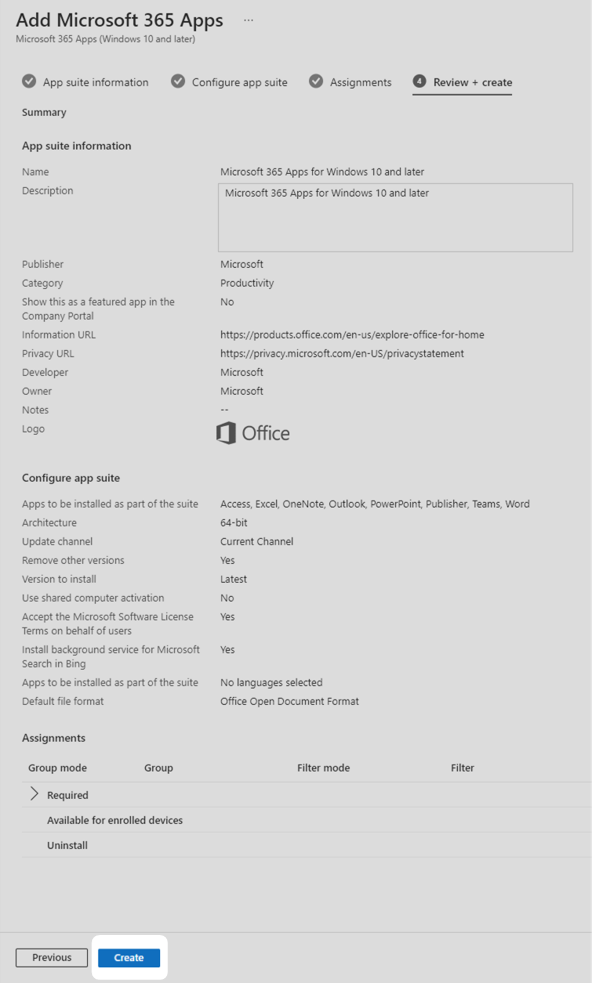
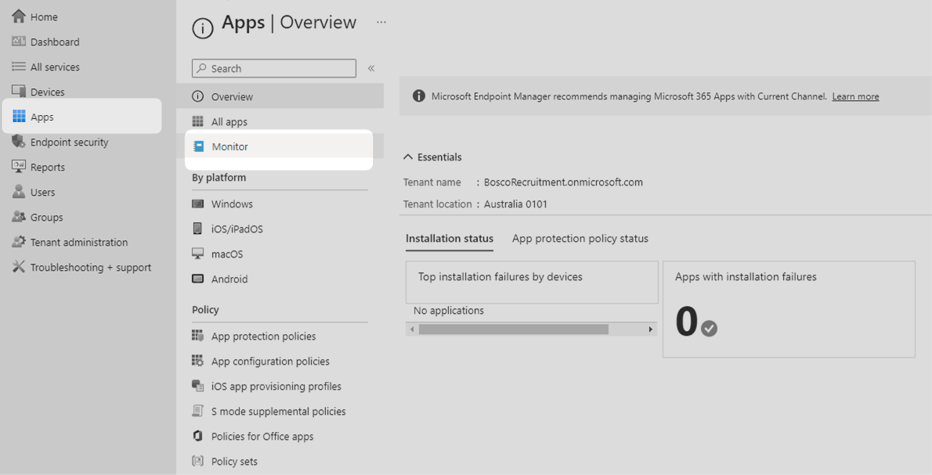
7. To verify that apps are being deployed successfully, administrators can check the dashboard. From the Microsoft Intune main menu, select Apps then Monitor.
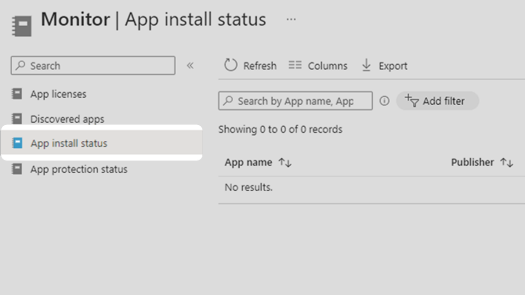
8. Select App install status. This will also show failed updates and can be used to verify device update compliance.
Identify missing patches with a vulnerability scanner
This technical example uses Microsoft’s in-built vulnerability scanning to scan internet-facing services. Microsoft automatically scans production assets daily with the most recent vulnerability signatures to identify potential security risks and remediate them.
Microsoft’s in-built auto-update tool is sufficient in identifying when Office products are out of date and have security vulnerabilities. If the above steps were followed, Office apps will be sufficiently protected.
Your organisation may wish to deploy an agent-based vulnerability scanner to scan any applications that are outside of the Microsoft 365 ecosystem. There are commercial solutions available that can be deployed via Microsoft Intune. Alternatively, administrators may wish to opt-in for Microsoft’s 'Block vulnerable applications' public preview which scans enrolled devices for applications which contain security vulnerabilities. This feature is still in beta and may not be sufficiently capable of replacing existing agent-based vulnerability scanning tools.
Remove unsupported products
It is up to IT staff to consider the configuration of their organisation and determine what installed applications are and are not supported. Any apps deployed via Microsoft Intune should be verified to ensure they are still supported by the vendor. If an unsupported application is required, IT staff should consider additional mitigations to maintain security, for example, using conditional access to only permit the application to run on accounts with reduced privileges.
