Application control restricts the ability of an application to run or install on a device. Application control makes it harder for users to intentionally or unintentionally install unwanted or malicious software.
Before you begin
Review the Small business cloud security guides introduction before you use this technical example. The introduction includes steps you should take before you begin, including:
- Check that you have a compatible Microsoft 365 subscription. This technical example requires a subscription to Microsoft 365 Business Premium (or equivalent).
- Enrol your compatible devices in Intune. Microsoft has published guidance on enrolling Windows devices in Intune.
The steps taken in this technical example require an account with 'Intune Administrator’ or ‘Global Administrator’ privileges.
Why you should implement application control
Application control restricts the ability of an application to run or install on a device. Application control makes it harder for users to intentionally or unintentionally install unwanted or malicious software.
Application control can be implemented in a variety of ways. In this example we have used Microsoft Defender Application Control, also known as Windows Defender Application Control (WDAC). Configuring the policy this way restricts all users to only be able to run Windows Components, Microsoft Store apps and reputable apps as defined by Microsoft’s Intelligent Security Graph.
This method was chosen due to the needs of our example business as well as for ease of applicability and maintenance of the policy. Note that businesses that require applications which are blocked by the Microsoft Intelligent Security Graph should consider other solutions, such as, using the WDAC wizard to explicitly allow applications that are business critical. Alternatively, businesses could use third party application control programs.
We recommend that each business considers their own specific needs and situation and apply application control as appropriate. This technical example uses Microsoft 365 Office apps and web-based applications to perform their day to day tasks. This means they don’t require any specific rules to allow software that is critical to their business. If your business needs to allow specific applications, consider using third party software or the WDAC wizard to create specific rules for the software you require. The WDAC wizard is an open-source application that was built to provide a more user-friendly way to create, edit and merge Application Control policies.
Requirements for application control
This technical example is adapted from Essential Eight maturity level one. It is designed to meet the intent of the following requirement:
- The execution of executables, software libraries, scripts, installers, compiled HTML, HTML applications and control panel applets is prevented on workstations from within standard user profiles and temporary folders used by the operating system, web browsers and email clients.
This technical example demonstrates one way to implement application control for organisations with resourcing constraints. The technical example uses Windows Defender Application Control to block applications that are not trusted by Microsoft’s Intelligent Security Graph. This solution requires minimal resources to implement and maintain but does not restrict executable to the full extent described in Essential Eight maturity level one. Before following this technical example, organisations should consider if it appropriately addresses their identified risks.
What this technical example covers
This technical example demonstrates an application control implementation for Microsoft 365 Intune configured devices.
Organisations that use other, business critical third-party applications should not rely on Microsoft’s Intelligent Security Graph to allow their apps to run and should considers using the WDAC wizard to create explicit allow rules or use a 3rd party application control solution.
Application control should be implemented for all organisational users. If you are unsure whether application control should be implemented for a particular user, consider if that user can access sensitive data or perform sensitive actions on your network, if they can, they should likely be considered an organisational user and application control should be implemented.
Technical example
1. Ensure that you are in the Microsoft Intune admin center. Select Devices in the main menu then select Configuration profiles. Select Create profile from the menu items at the top of the page.
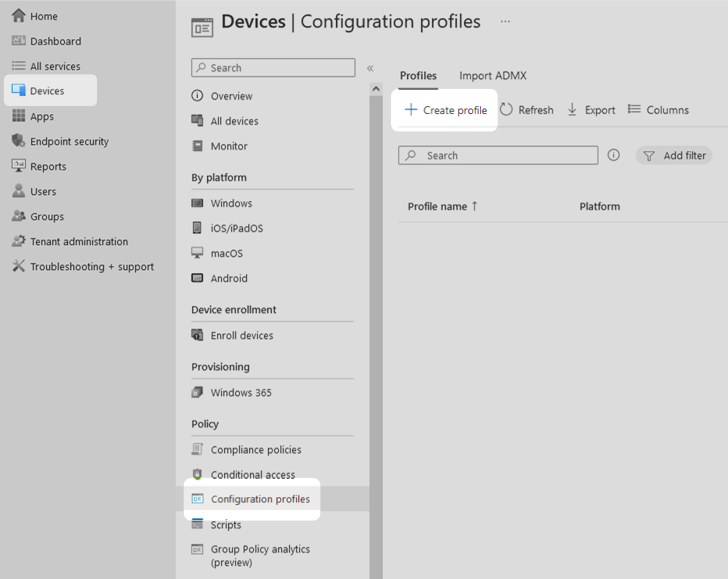
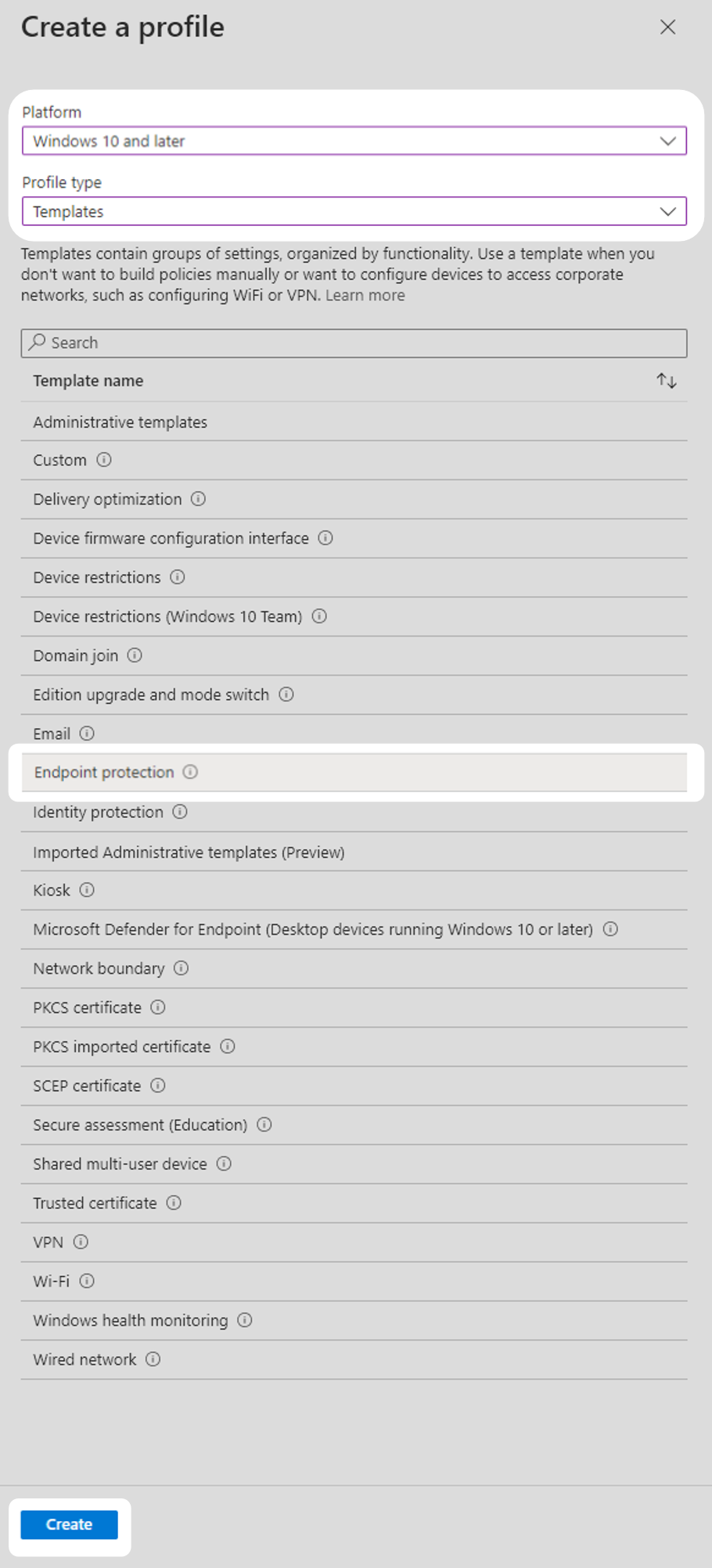
2. Under the Platform heading, select the platform you are using from the drop-down menu. In this technical example, Windows 10 and later was selected. Under the Profile type heading, select Templates. Under the Template name heading select Endpoint protection, then select Create.
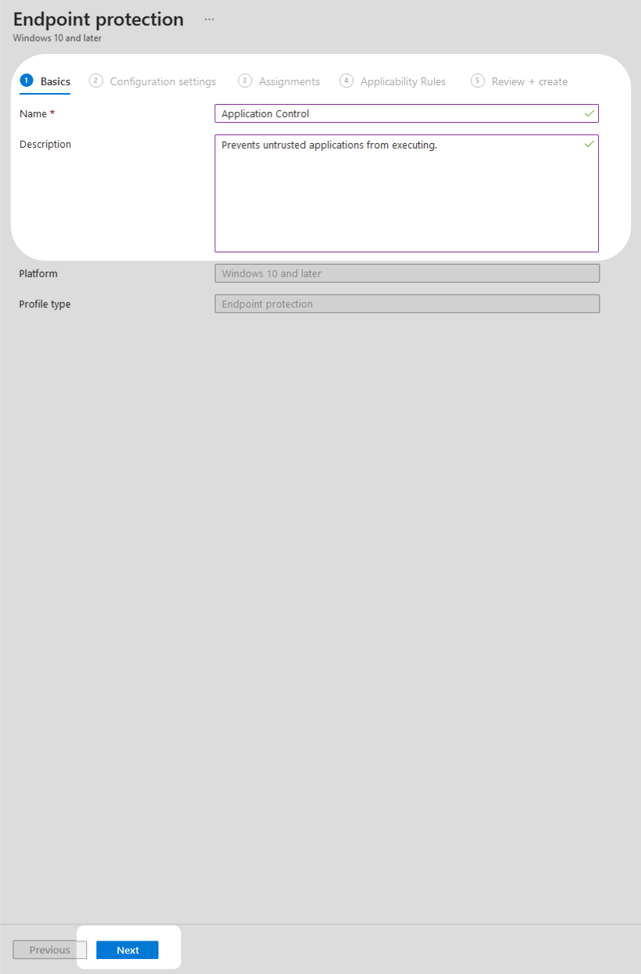
3. Name the configuration profile and give it a description then select Next.
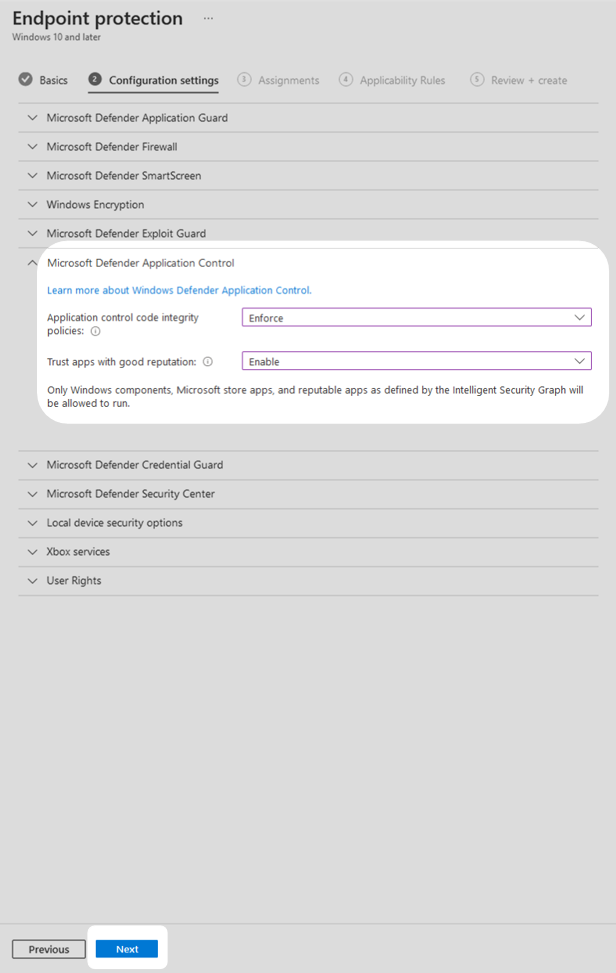
4. Select Microsoft Defender Application Control and set Application control code integrity policies to Enforce. Then set Trust apps with good reputation to Enable. Select Next.
Note: in this technical example application control is enforced immediately. Organisations should consider first putting application control into ‘Audit’ mode and tracking events in event viewer. If you find business critical applications will be blocked when switching to enforced mode, please consider using the WDAC wizard to create explicit allow rules or third-party software to ensure operational continuity.
5. Assign this configuration profile to all devices, by pressing Add all devices then select Next.
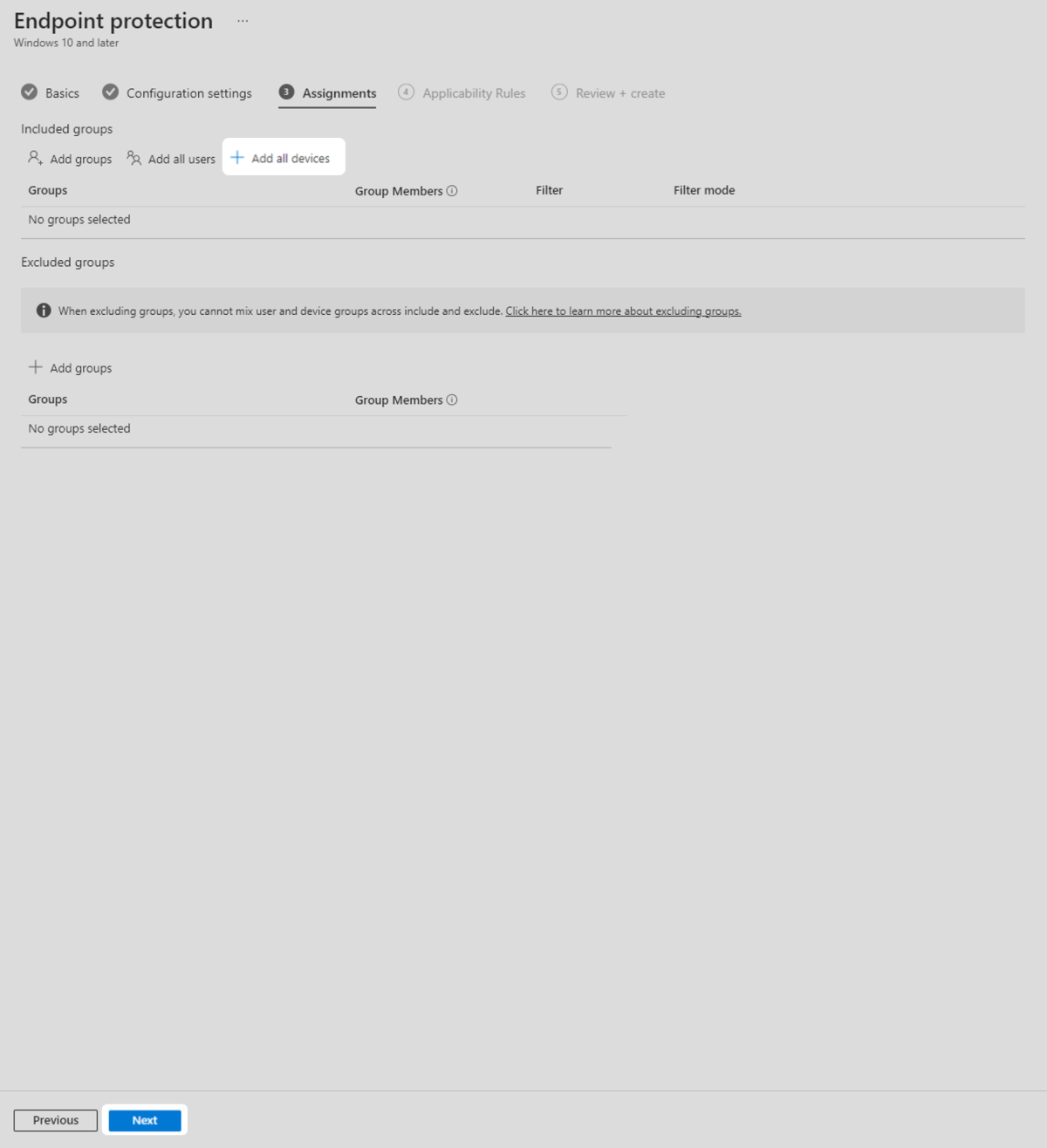
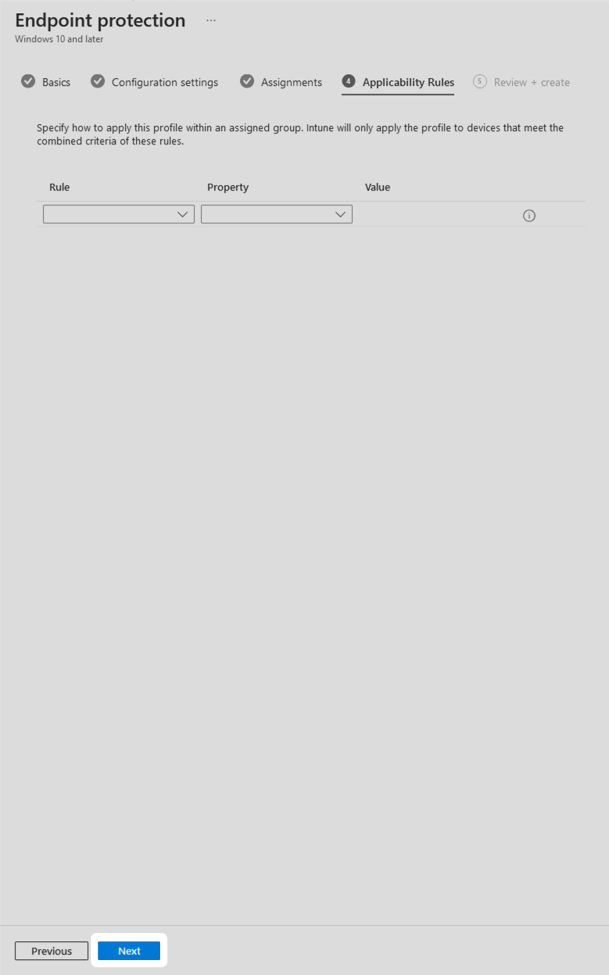
6. Configure any applicability rules that are relevant to your organisation then select Next. In this technical example, applicability rules were not required.
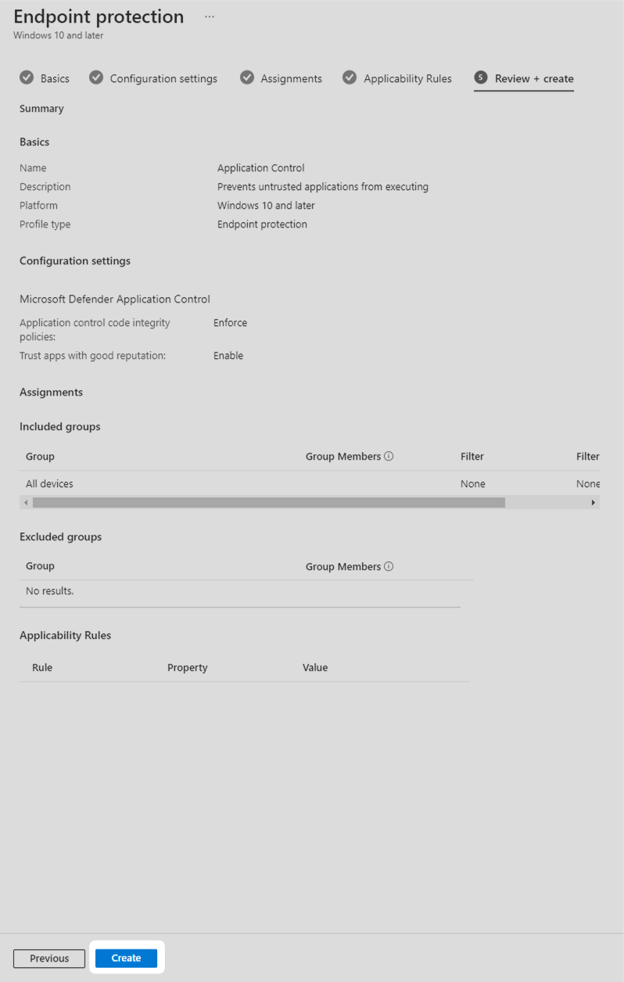
7. Review the configuration profile is set properly and select Create.
After implementing application control, test it is working by attempting to run a script that is innocuous but not trusted by the Security Intelligence Graph.
Known limitations
This approach can be quite effective in blocking execution of obviously malicious programs. However, it may block some programs that have legitimate uses and does not offer a way for users and administrators to make a special exemption to run the program. With the broad availability of web browser-based applications, the added security benefits of this implementation may be seen to outweigh the inconveniences.
Furthermore, programs that have legitimate as well as malicious uses will likely be able to execute. These include tools that allow a remote user to control a computer. In most cases these will require convincing the legitimate user to install the tool, and hence user education will be required to supplement the technical mitigation.
Note: This approach to application control does not meet the requirements for the Essential Eight maturity model due to the use of Microsoft Intelligence Security Graph. If you are aiming to meet Essential Eight requirements, please consider using the WDAC Wizard or a third-party application control solution.
