Configuring macro settings protects an organisation’s systems from malicious macros. Macros are powerful tools. They were introduced to improve productivity however their functionality can also be used by cyber criminals to compromise a user’s system.
Before you begin
Review the Small Business Cloud Security Guides introduction before you use this technical example. The introduction includes steps you should take before you begin, including:
- Check that you have a compatible Microsoft 365 subscription. This technical example requires a subscription to Microsoft 365 Business Premium (or equivalent).
- Enable security defaults in Azure Active Directory. Microsoft has published guidance on enabling Security defaults.
- Enrol your compatible devices in Intune. Microsoft has published guidance on enrolling Windows devices in Intune.
The steps taken in this technical example require an account with Intune Administrator or Global Administrator privileges.
Why you should configure Microsoft Office macro settings
Configuring macro settings protects an organisation’s systems from malicious macros. Macros are powerful tools. They were introduced to improve productivity however their functionality can also be used by cyber criminals to compromise a user’s system. Malicious macros are widespread with capabilities that include:
- Accessing and exfiltrating sensitive information.
- Downloading and executing malware (including ransomware) on a victim’s network.
- Corrupting or erasing data.
Configuring macro settings to restrict their use is an essential measure for organisations to protect against malware infections. Disabling macros for users without a demonstrated business requirement to use them reduces the number of people that can introduce a malicious macro to an organisation’s environment. This measure is strengthened by preventing standard users from changing macro security settings. For many organisations, disabling macros is not a viable option for all users. In such cases, the risk of running malicious macros can be mitigated by enabling macros only for users who have a demonstrated business requirement to use them, and only on applications where macros are required. Regardless of whether or not an organisation allows macros, macro antivirus scanning should be enabled.
Requirements for Microsoft Office macro settings
This technical example is adapted from Essential Eight maturity level one. It is designed to meet the following requirements:
- Microsoft Office macros are disabled for users that do not have a demonstrated business requirement.
- Microsoft Office macros in files originating from the internet are blocked.
- Microsoft Office macro antivirus scanning is enabled.
- Microsoft Office macro security settings cannot be changed by users.
What this technical example covers
This technical example demonstrates one way to securely configure Microsoft Office macro settings. The technical example includes two configuration profiles:
- A profile for employees with a demonstrated business requirement to run macros.
- A profile for employees without a demonstrated business requirement to run macros.
It also demonstrates one way to achieve macro antivirus scanning using Microsoft Defender Antivirus.
This technical example is designed for organisations with limited cyber security resources and expertise. Organisations with advanced expertise should consider following ASD's ACSC’s more detailed macro security guidance.
Technical example
Create a configuration profile for users without a demonstrated business requirement to use macros
Note: The steps below assume that organisations that require some users to run macros have created a security group for these users. Microsoft has published guidance on creating a security group.
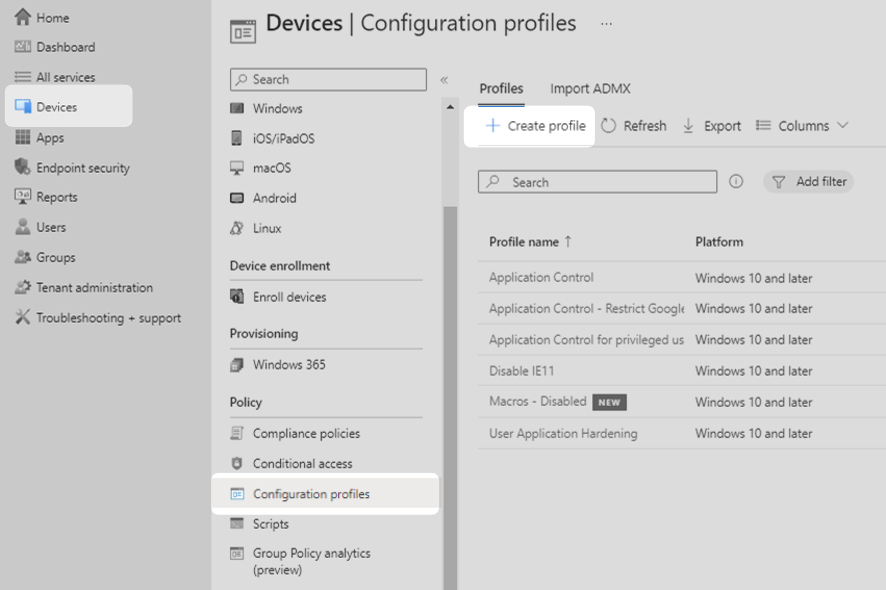
1. Log into the Microsoft Intune admin center. Select Devices in the main menu then select Configuration profiles. Select Create profile from the menu items at the top of the page.
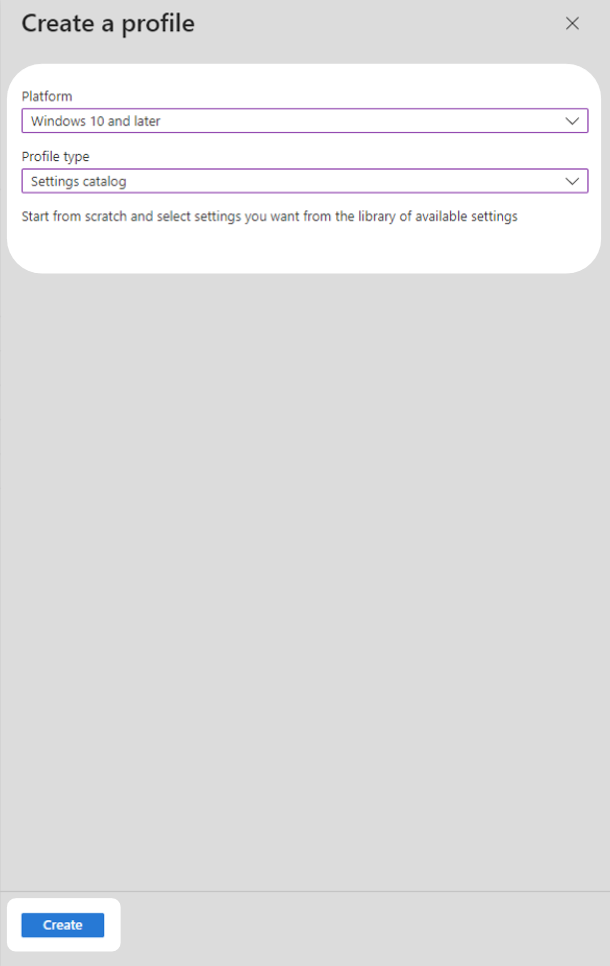
2. Under the Platform heading, select the platform you are using from the drop-down menu. In this technical example, Windows 10 and later was selected. Under the Profile type heading, select Settings catalog then select Create.
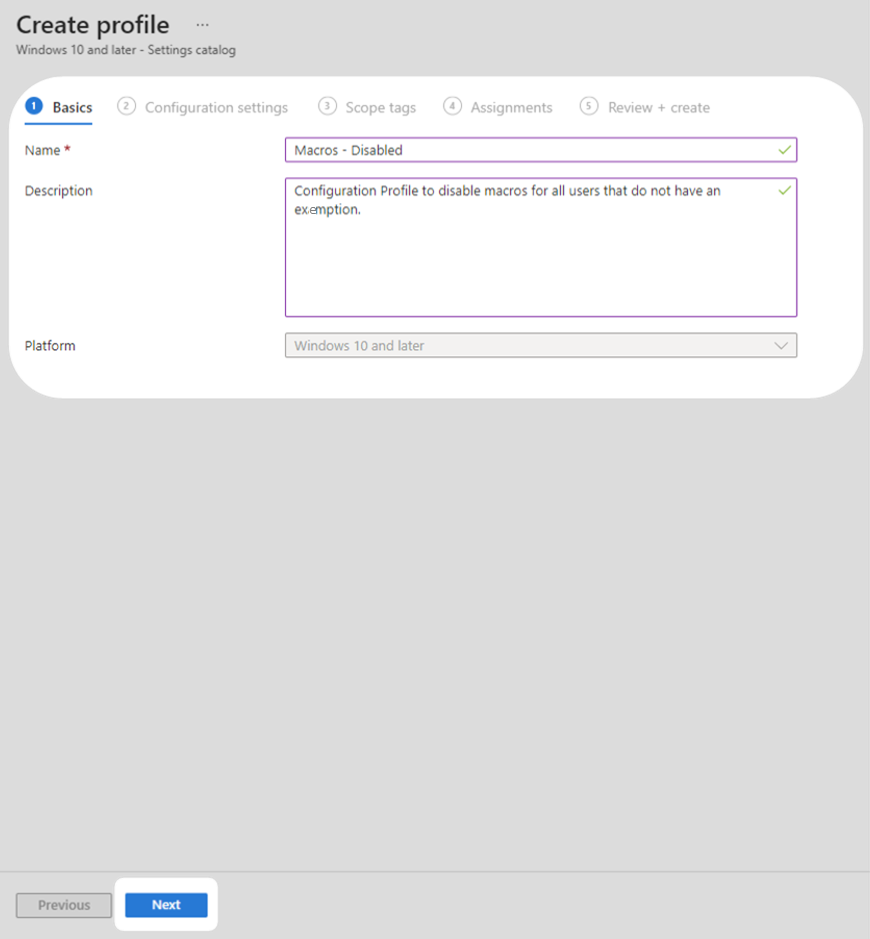
3. Input a name and description for the configuration profile then select Next.
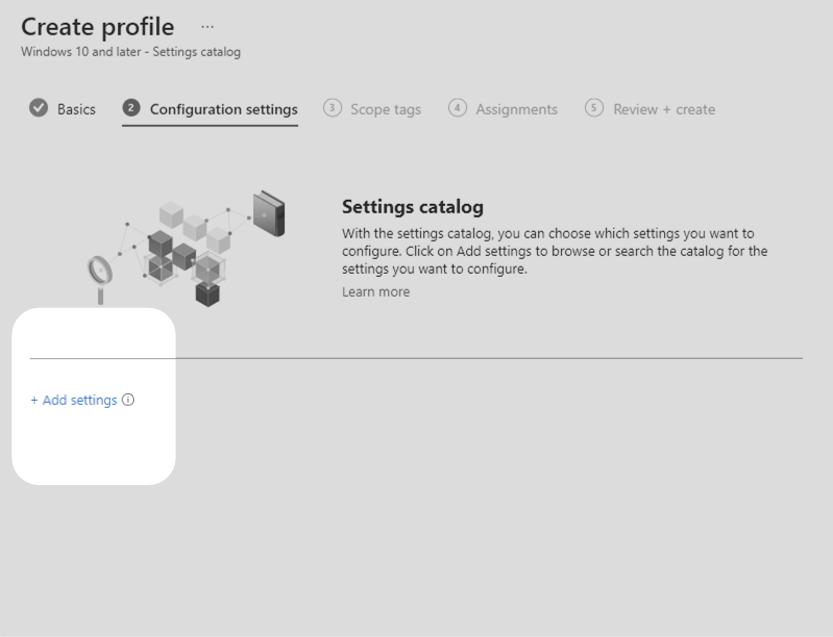
4. Select + Add settings to view the Settings picker.
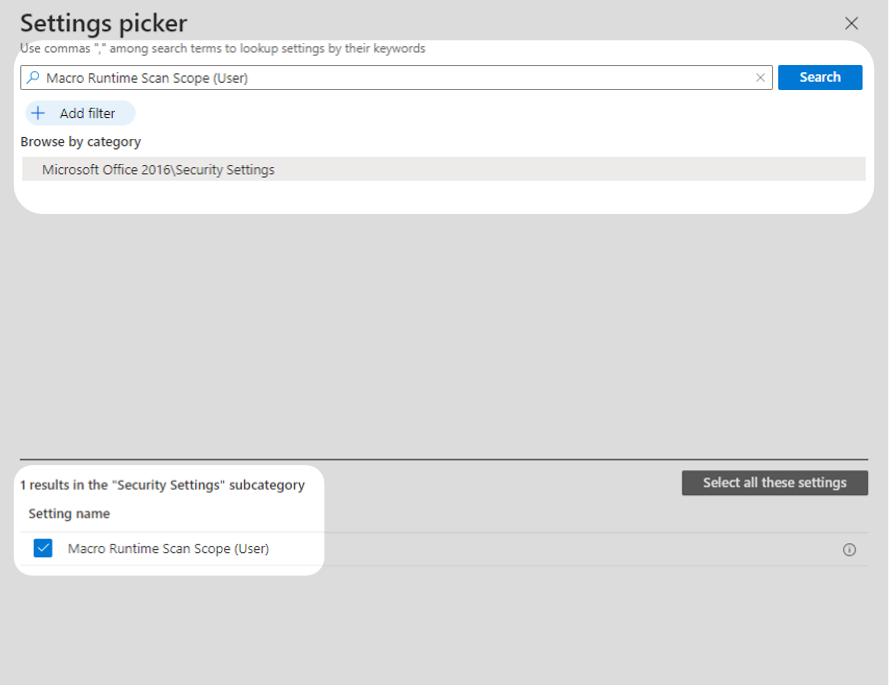
5. From the Settings picker, search for and select the following two settings:
(a) Disable VBA for Office Applications (User)
(b) Macro Runtime Scan Scope (User)
The settings you select will appear in the left-hand pane of your window.
6. Configure the settings you selected:
(a) Disable VBA for Office Applications (User) - Select Enabled.
(b) Macro Runtime Scan Scope (User) - Select Enabled then select Enable for all documents from the drop-down menu.
Once you have configured the settings, select Next
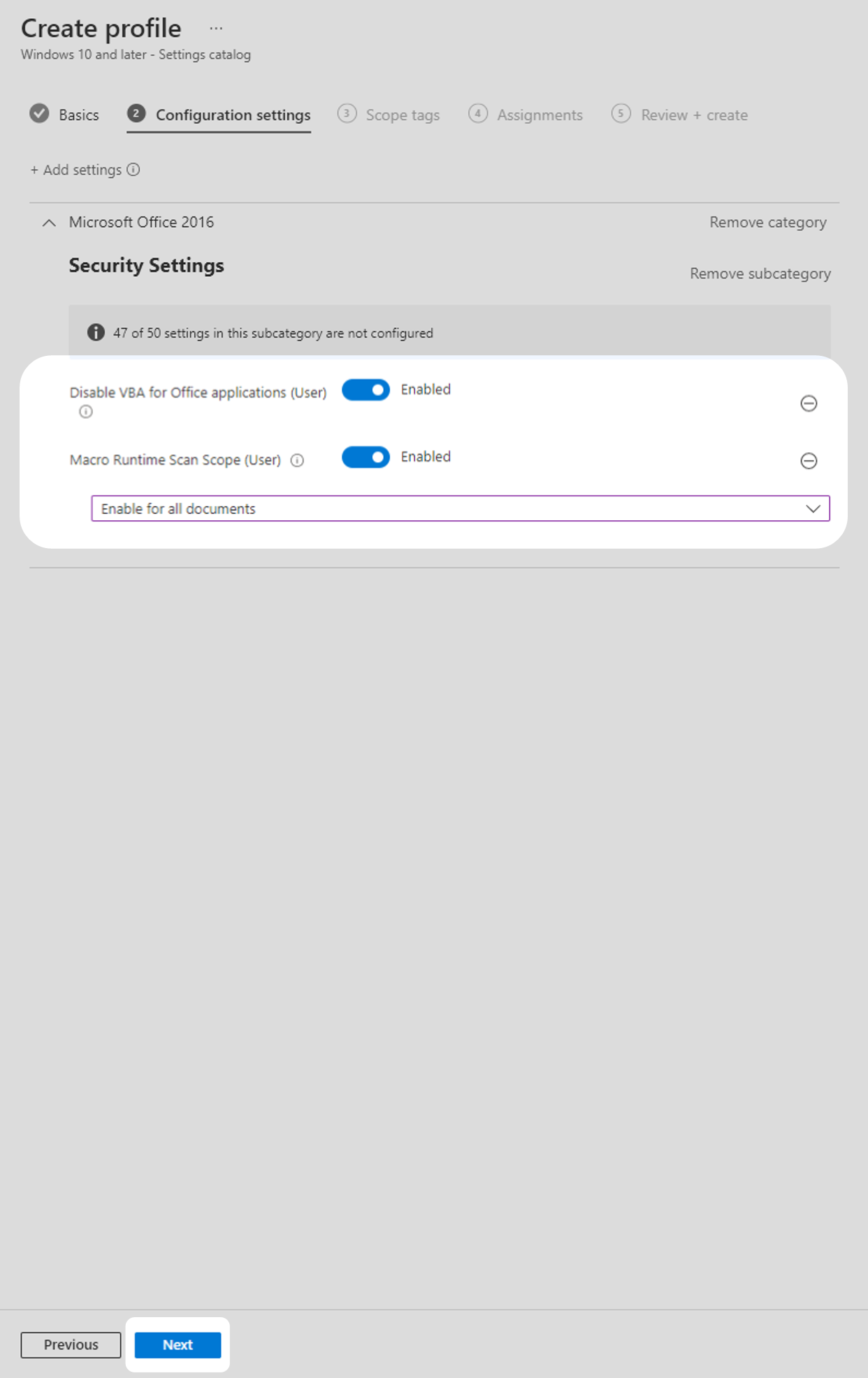
Note: VBA stands for Visual Basic for Applications, the language used to write Macros. Disabling VBA will prevent all macros from running when this policy is applied.
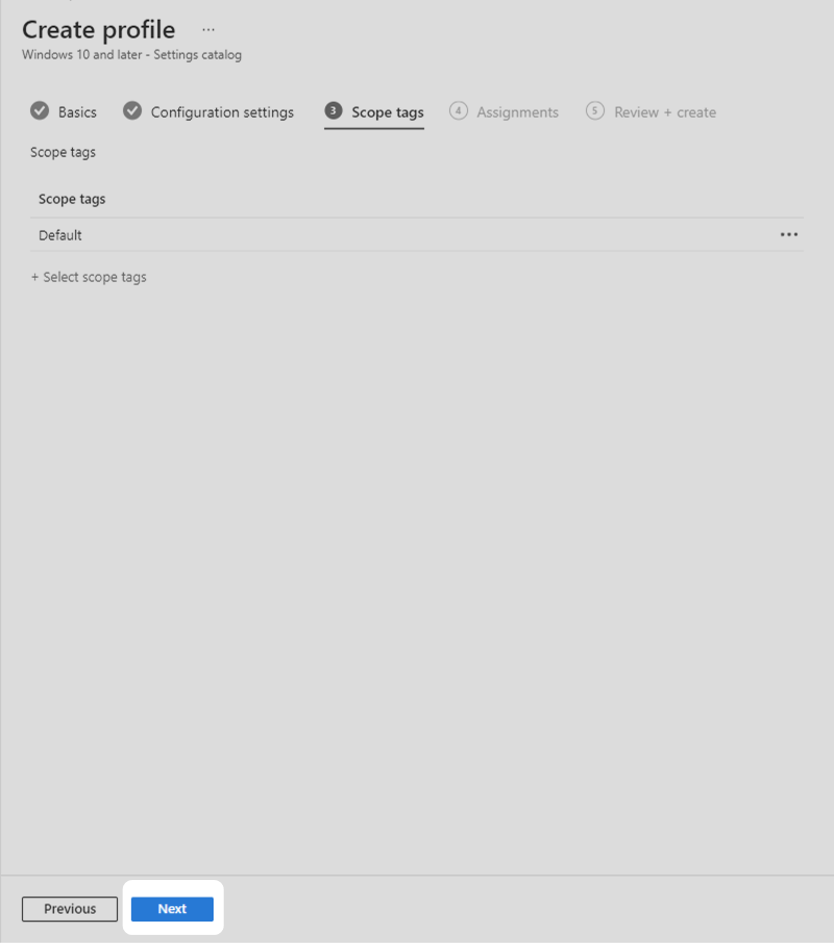
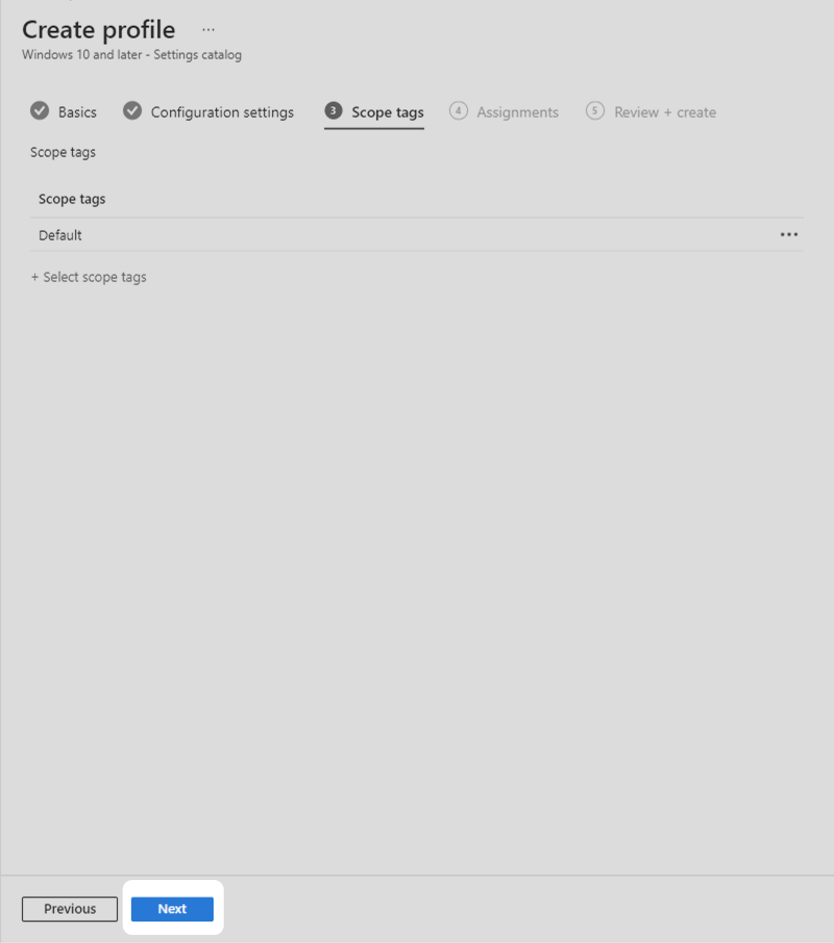
7. After completing the configuration settings step, you will be given an opportunity to select scope tags. This technical example progressed with the default settings for this step. Your organisation should configure scope tags according to its needs then select Next.
8.Under the Included groups heading, select Add all users.
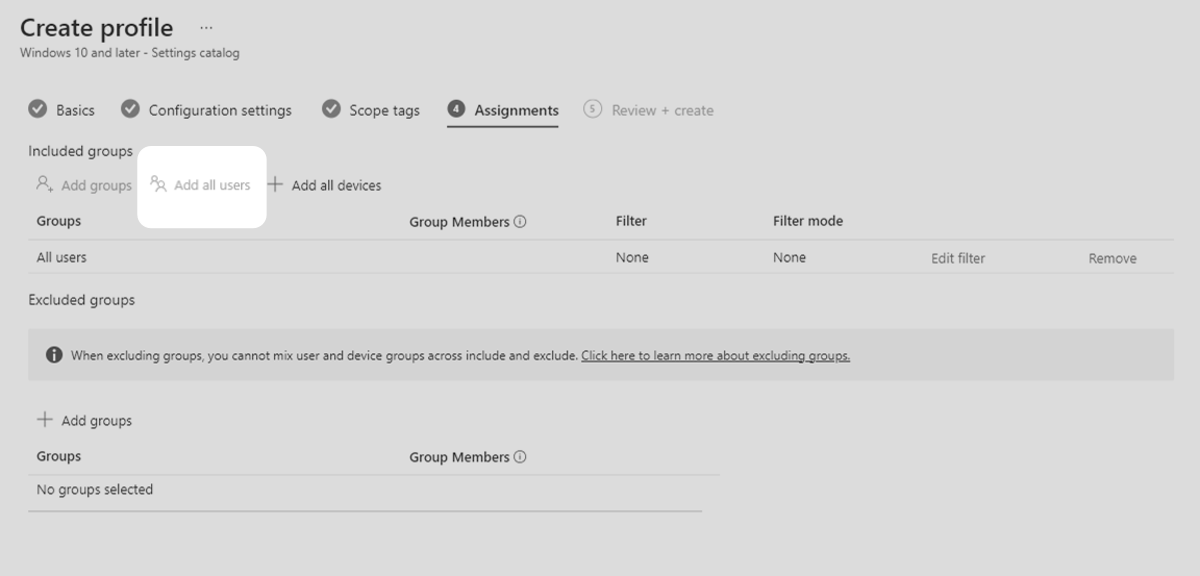
9. If your organisation has a group of users that have a demonstrated business requirement to use macros, you can exclude them from this configuration profile. Under the Excluded groups heading, select Add groups, select the security group that requires macros then click the Select button at the button at the bottom of the panel. Select Next to continue to the next step.
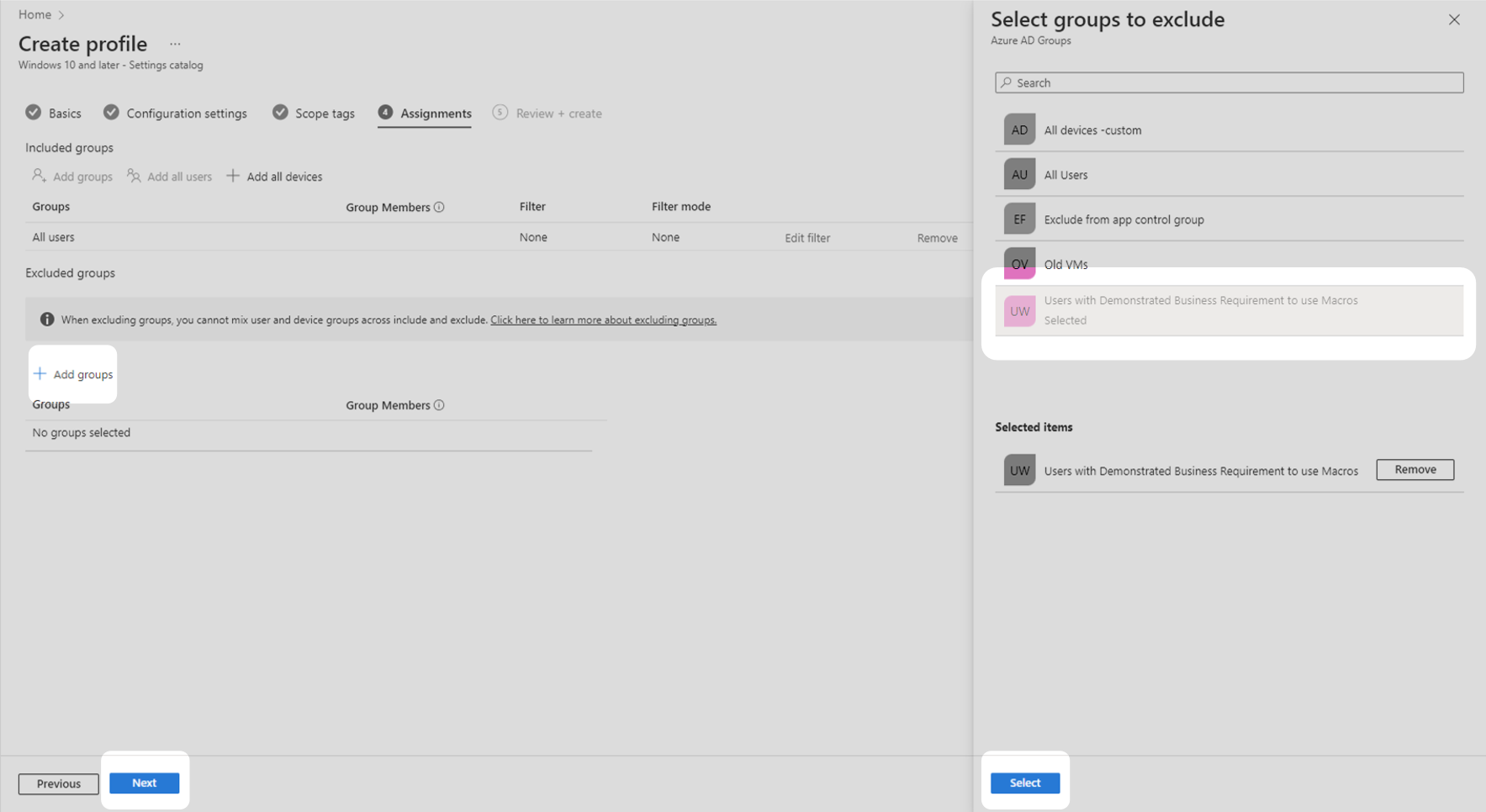
10. Confirm that the profile has been configured as intended then select Create.
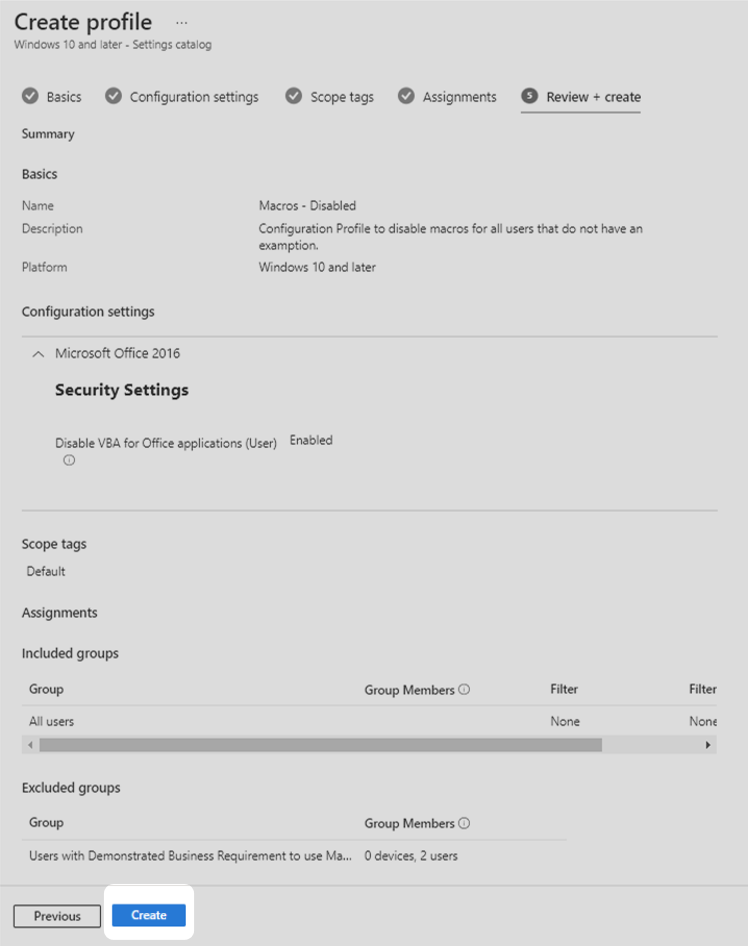
Create a configuration profile for users with a demonstrated business requirement to use macros
1. Ensure that you are still in the Microsoft Intune admin center. Select Devices in the main menu then select Configuration profiles. Select Create profile from the menu items at the top of the page.

2. Under the Platform heading, select the platform you are using from the drop-down menu. In this technical example, Windows 10 and later was selected. Under the Profile type heading, select Settings catalog then select Create.

3. Input a name and description for the configuration profile then select Next.
4. Select + Add settings to view the Settings picker.

5. Search for and select the settings shown in Table 1 below.
| Setting category | Setting name |
|---|---|
| Defender | Block Win32 API calls from Office macros |
| Microsoft Access 2016\Application Settings\Security\Trust Center |
Block macros from running in Office files from the Internet (User) |
| Microsoft Excel 2016\Excel Options\Security\Trust Center |
Block macros from running in Office files from the Internet (User) |
| Microsoft Office 2016\Security Settings | Macro Runtime Scan Scope (User) |
| Microsoft Outlook 2016\Security\Security Form Settings | Security setting for macros (User) |
| Microsoft PowerPoint 2016\PowerPoint Options\Security\Trust Center |
Block macros from running in Office files from the Internet (User) |
| Microsoft Project 2016\Project Options\Security\Trust Center | VBA Macro Notification Settings (User) |
| Microsoft Publisher 2016\Security\Trust Center | VBA Macro Notification Settings (User) |
| Microsoft Visio 2016\Visio Options\Security\Trust Center |
Block macros from running in Office files from the Internet (User) |
| Microsoft Word 2016\Word Options\Security\Trust Center |
Block macros from running in Office files from the Internet (User) |
6. Configure the settings you selected, as shown in Table 2 below.
| Application | Setting name | Setting configuration |
|---|---|---|
| Defender | Block Win32 API calls from Office macros | Select Block from the drop-down menu. |
| Access | Block macros from running in Office files from the Internet (User) | Select Enabled. |
| VBA Macro Notification Settings (User) |
Select Enabled. If there is a demonstrated business requirement to use macros for this app, select disable all with notification from the drop-down menu. Otherwise, select disable all without notification. |
|
| Excel | Block macros from running in Office files from the Internet (User) | Select Enabled. |
| VBA Macro Notification Settings (User) |
Select Enabled. If there is a demonstrated business requirement to use macros for this app, select disable all with notification from the drop-down menu. Otherwise, select disable all without notification. |
|
| Office | Macro Runtime Scan Scope (User) | Select Enabled then from the drop down menu select Enable for all documents. |
| Outlook | Security setting for macros (User) |
Under Outlook Security Mode (User) select Enabled then choose your preferred configuration from the drop-down menu. |
| PowerPoint | Block macros from running in Office files from the Internet (User) | Select Enabled. |
| VBA Macro Notification Settings (User) |
Select Enabled. If there is a demonstrated business requirement to use macros for this app, select disable all with notification from the drop-down menu. Otherwise, select disable all without notification. |
|
| Project | VBA Macro Notification Settings (User) |
Select Enabled. If there is a demonstrated business requirement to use macros for this app, select disable all with notification from the drop-down menu. Otherwise, select disable all without notification. |
| Publisher | VBA Macro Notification Settings (User) |
Select Enabled. If there is a demonstrated business requirement to use macros for this app, select disable all with notification from the drop-down menu. Otherwise, select disable all without notification. |
| Visio | Block macros from running in Office files from the Internet (User) |
Select Enabled. |
| VBA Macro Notification Settings (User) |
Select Enabled. If there is a demonstrated business requirement to use macros for this app, select disable all with notification from the drop-down menu. Otherwise, select disable all without notification. |
|
| Word | Block macros from running in Office files from the Internet (User) | Select Enabled. |
| VBA Macro Notification Settings (User) |
Select Enabled. If there is a demonstrated business requirement to use macros for this app, select disable all with notification from the drop-down menu. Otherwise, select disable all without notification. |
Note: The examples shown in Tables 1 and 2 are not exhaustive, they demonstrate one of several ways to configure Office macro settings. Other configuration options are available, including enabling only digitally signed macros. Organisations should choose the configuration that best matches their risk profile and organisational needs. Organisations should also consider only installing office applications they require to reduce their attack surface.
The VBA Macro Notification Setting Disable all with notification disables macros by default with a notification that allows users to enable macros on a case-by-case basis.
The VBA Macro Notification Setting Disable all without notification disables macros entirely for the configured application.
7. After configuring settings, select Next to progress to the next step.
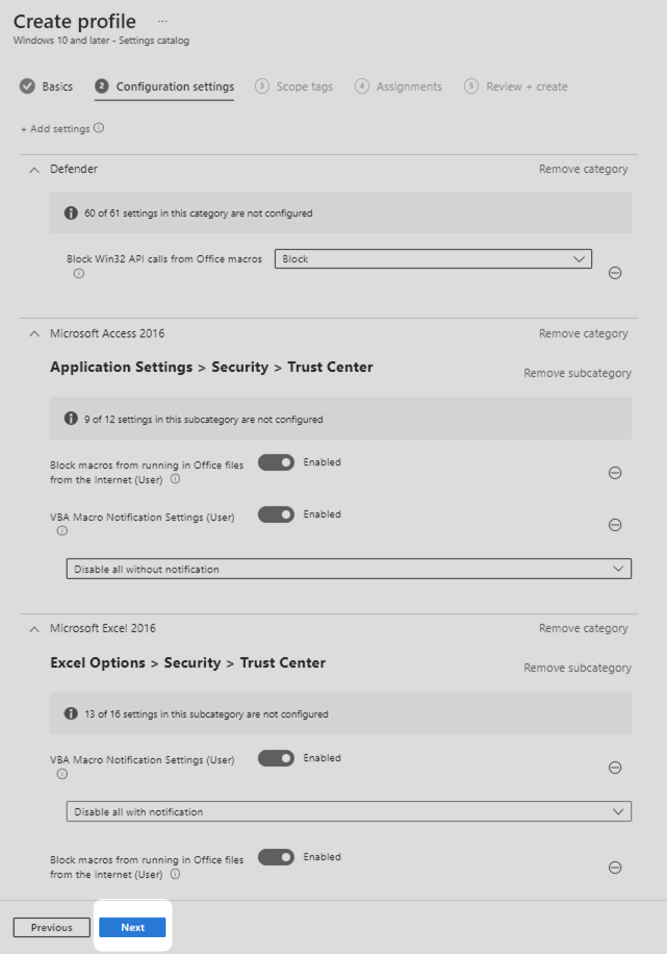
8. After completing the configuration settings step, you will be given an opportunity to select scope tags. This technical example progressed with the default settings for this step. Your organisation should configure scope tags according to its needs then select Next.
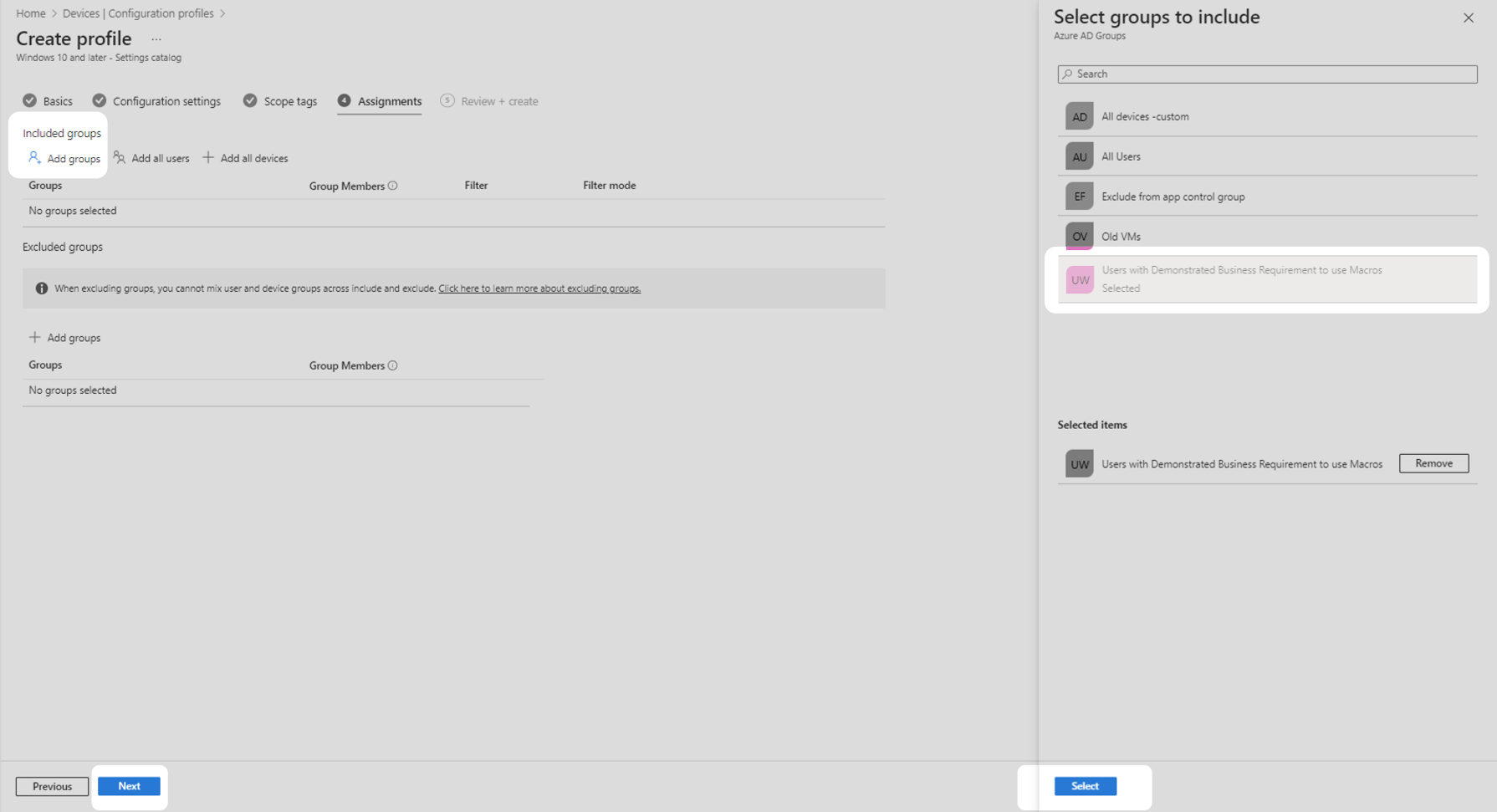
9. Under the Included groups heading, select Add groups, select the security group that requires macros then click the Select button at the button at the bottom of the panel. Select Next to continue to the next step.
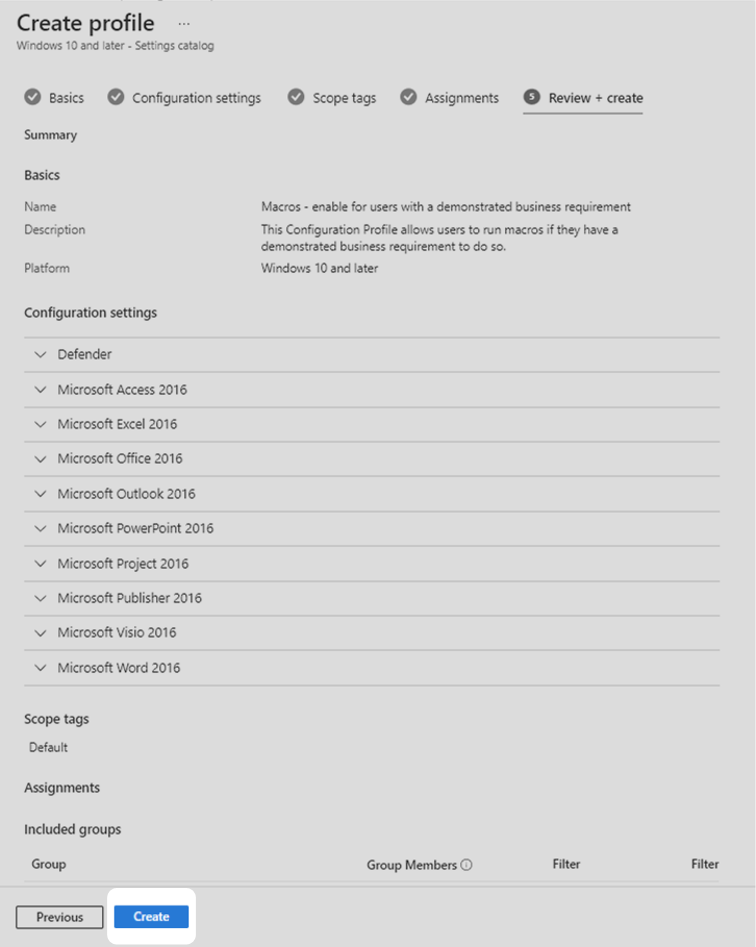
10. Confirm that the profile has been configured as intended then select Create.
Configure Microsoft Office antivirus scanning
Scanning for malicious macros is an important mitigation for organisations that cannot disable macros entirely. This technical example configured a setting called Macro runtime scan scope to enable runtime scanning for all files that have macros enabled. This setting uses Microsoft’s Antimalware Scan Interface (AMSI).
AMSI is an open interface for applications to, at runtime, request a synchronous scan by a compatible antivirus or security solution. There are several antivirus solutions that interface with AMSI. The antivirus solution chosen for this technical example is Microsoft Defender Antivirus. Microsoft Defender Antivirus interfaces with AMSI by default. If your organisation chooses a different antivirus solution, ensure that it supports and is configured to use AMSI.
