Introduction
Cloud computing offers a range of potential cybersecurity benefits for cloud consumers to leverage, providing access to advanced security technologies, shared responsibilities, fine-grained access management, comprehensive monitoring and highly redundant geographically dispersed cloud services. For many organisations, cloud computing can provide significant improvements to their cybersecurity, mitigating the risk of many current cyberthreats.
While cloud computing can significantly enhance an organisation’s cybersecurity, it also presents other risks that need to be considered, such as multi-tenancy architectures, reduction in visibility of the physical and virtualisation layers, and possible foreign interference.
At its core, cloud computing involves outsourcing a part, or all, of a consumer’s information technology (IT) capability to a Cloud Service Provider (CSP). This outsourcing brings a reduction in control and oversight of the technology stack, as the CSP dictates both the technology and operational procedures available to the cloud consumers using its cloud services.
Cloud computing, by default, does not provide improved cybersecurity without effort on behalf of the cloud consumer to perform their security responsibilities in securing the cloud. If not properly managed, maintained and configured, it can increase the risk of a cybersecurity incident occurring. Cloud consumers need to consider the benefits and risks of cloud computing, including their own responsibilities for securing the cloud and determining whether cloud computing meets their security needs and risk tolerance.
One of the biggest barriers to cloud consumers adopting cloud computing is the difficulty identifying and understanding the risks of using a CSP and its cloud services. Cloud computing presents a uniquely complex and layered technology stack that is rapidly evolving and resists traditional point-in-time assessments. This publication guides CSPs, cloud consumers and IRAP assessors on how to perform a comprehensive assessment of a CSP and its cloud services so that a risk-informed decision can be made about its suitability to store, process and communicate data.
The assessment and authorisation process detailed in this publication uses the security requirements and cloud guidance detailed in the Department of Home Affairs’ Protective Security Policy Framework (PSPF) and the Information security manual (ISM). These documents provide the requirements and controls for cloud consumers to use in the assessment of the CSP, its cloud services and a cloud consumer’s own systems.
The terminology and definitions used in this publication for cloud computing are consistent with the National Institute of Standards and Technology’s (NIST) Special Publication (SP) 800-145, The NIST Definition of Cloud Computing.
Audience
This publication is intended for CSPs, Infosec Registered Assessors Program (IRAP) assessors and Non-Corporate Commonwealth Entities (NCCEs, referred to as cloud consumers in this publication) who are subject to the Public Governance, Performance and Accountability Act 2013 to the extent consistent with legislation.
This publication assists and guides IRAP assessors, cloud consumer’s cybersecurity practitioners, cloud architects and business representatives on how to perform an assessment of a CSP and its cloud services, and the cloud consumer’s own self-developed systems hosted in the cloud.
While this publication is primarily intended for cloud consumers, this guidance can be used by any organisation considering cloud computing.
Cloud computing vs self-managed
Organisations who manage and secure their own IT infrastructure, such as an on-premise environment, need to consider as part of their risk assessment of cloud computing, the risks of not transitioning to cloud computing.
An organisation who owns and manages its own IT infrastructure is responsible for securing all aspects of it, including achieving the desired security baseline, maintaining it and updating it as malicious actor tradecraft evolves; depending on the size of the environment, this may necessitate significant effort and resources on behalf of the organisation to achieve this.
As part of an organisation’s examination of cloud computing, it needs to consider its own capabilities to secure their systems and protect their data from current and future cyberthreats. If an organisation’s basic security practices such as patching, upgrading and system hardening are ineffective or inconsistent, cloud computing may provide significant security improvements. By transferring some security responsibilities to the CSP, an organisation can prioritise other, more specific security mitigations such as access control, authentication and monitoring. In addition to transferring some security responsibilities, leveraging the advanced security technologies available from many CSPs can provide substantial cybersecurity improvements beyond what is feasible when an organisation owns and manages its own IT infrastructure.
While cloud computing can improve an organisation’s cybersecurity, this can only be achieved by understanding the shared responsibility between the cloud consumer and the CSP, and which party is responsible for securing which parts of the cloud. The cloud consumer also needs to plan, design and configure the cloud services it is using to achieve its desired security baseline. The cloud consumer then needs to monitor the CSP, its cloud services and its own systems and respond to any changes to the security baseline that are outside the cloud consumer’s risk tolerances.
Principles
This publication, in conjunction with the ISM, Cloud security assessment report template and Cloud controls matrix (CCM), is designed to assist cloud consumers to identify the risks associated with a CSP and its cloud services, and make a risk-informed decision about using cloud computing.
To support this self-authorisation and risk-based decision by cloud consumers is the independent assessment of a CSP and its in-scope cloud services by an IRAP assessor. This assessment forms the basis of the review by cloud consumers of a CSP and its cloud services. This assessment is performed against the controls in the ISM and other related guidance from the Australian Signals Directorate (ASD), such as this publication. The IRAP assessor will document their findings in the Cloud security assessment report template, which once completed will be provided to the CSP. The report can then be shared with any NCCE who is considering using the CSP’s cloud services.
One of the key principles of the assessment is the separation of the CSP and its cloud services. This emphasises the importance of assessing and reviewing the security fundamentals of the CSP itself. Cloud consumers need to ensure the CSP itself is operating securely and meets the cloud consumer’s security and risk requirements.
Adopting cloud computing requires a degree of trust given to the CSP to handle a cloud consumer’s data. The cloud consumer needs to gain enough assurance of the CSP so that this trust is not unwarranted. The other part of the assessment focuses on the specific cloud services of the CSP that are in scope of the assessment.
Each cloud service will be documented individually in the cloud security assessment report. This is so cloud consumers can review a cloud service without needing to read about other, unrelated cloud services to obtain the required information to make a risk-based decision about using a particular cloud service.
To help cloud consumers maintain awareness of the risks of using a CSP and its cloud services, CSPs are responsible for maintaining the accuracy and currency of the report between independent assessments by adding addendums to the cloud security assessment report. These addendums are to detail any changes that have occurred to the CSP or its cloud services that result in any part of the original report becoming inaccurate. New addendums are to be communicated to any cloud consumer who has used the cloud security assessment report as part of their assessment of the CSP. This supports cloud consumers to maintain continual awareness of the CSP and its cloud services and respond to any changes that impact the risks and the security baseline of the systems.
Department of Home Affairs’ Protective Security Policy Framework
The PSPF has been developed to assist NCCEs to protect their people, information and assets, in Australia and overseas. The PSPF articulates government protective security policy. NCCEs, to the extent consistent with legislation, must apply the PSPF using a security risk management approach when using a CSP, its cloud services and their own systems. NCCEs remain accountable for their adherence to the PSPF and this accountability cannot be transferred to a CSP or other third-party.
Personnel security
As part of the cloud consumer’s review of a CSP to determine if it meets its security requirements and risk tolerance, the cloud consumer needs to consider the classification of the data it intends to use on the CSP’s cloud services, as well as the suitability of the CSP to store, process and transmit this data. Understanding the classification of the data to be used on a CSP’s cloud services will assist in identifying the personnel security requirements the CSP needs to adhere to.
To understand the personnel security risks to a cloud consumer’s data, cloud consumers need to assess the CSP’s personnel pre-employment screening and the CSP’s controls that prevent and detect its personnel accessing customer data without proper authorisation.
To manage, support and update their cloud services, CSPs require privileged access to perform these responsibilities. This is a risk that is common with most outsourcing arrangements, whereby an external party has some degree of privileged access to systems that handle customer data. This risk needs to be carefully considered and accepted by cloud consumers before any of their data is transferred to the CSP’s cloud services.
CSPs can implement additional controls to mitigate the risk of its personnel accessing or encountering its customers data without proper authorisation. If implemented effectively, these controls can significantly lower this risk by preventing, detecting and responding to any incidents of unauthorised access by its personnel. Cloud consumers, as part of their risk assessment of a CSP’s personnel security, need to consider these controls to determine the risk a CSP’s personnel poses to its data. These controls are:
- separation of duties, such as personnel with physical access to IT infrastructure not having logical access and vice versa
- data encryption at rest and in transit by default
- secure storage and customer supplied and/or management of encryption keys for customer data
- just in time and just enough access methodologies for its personnel’s access
- real-time monitoring to detect and log when CSP personnel access customers’ data, and the ability to quickly terminate any access that is unauthorised
- providing the cloud consumer with the capability to provide explicit approval before the CSP’s personnel access its data
- providing cloud consumers with flexible support arrangements including the ability to choose where support is provided from
- contractual clauses with customers that require the CSP to disclose to the cloud consumer any incidents of its personnel accessing, or encountering, the cloud consumer’s unencrypted data.
While the risk of a CSP’s personnel accessing or encountering its customers’ data cannot be eliminated, it can be significantly reduced with the implementation of the above controls.
The absence of effective controls to prevent and detect a CSP’s personnel accessing customer data also increases the risk that classified data will be accessed by personnel without an appropriate need-to-know, including those CSPs whose personnel hold an Australian Government security clearance. These CSPs will also be unlikely to be able to inform its cloud consumers of any incidents of unauthorised access to their data within a reasonable time period. The implementation and effectiveness of these controls needs to be carefully considered as part of a cloud consumer’s review of a CSP.
CSPs who store, process and communicate data marked up to OFFICIAL: Sensitive, are not required to have personnel with Australian Government security clearances to handle this classification of data. Cloud consumers only using data marked up to OFFICIAL: Sensitive need to ensure the CSP’s personnel pre-employment screening aligns to, or meets the intent of the pre-employment screening requirements detailed in the PSPF.
CSPs who store, process or communicate data classified at PROTECTED and above are required to have personnel who hold a current Australian Government security clearance commensurate with the classification of the data being stored, processed and communicated on the CSP’s systems. This requirement applies to any of the CSP’s personnel who have physical access to infrastructure that handles classified data, and to personnel with logical access (including potential logical access) to infrastructure that handles classified data.
Personnel security clearances, like technical controls, provide a degree of assurance that the personnel are suitable to have access to classified data. Personnel security clearances do not provide a guarantee against maleficence on behalf of the personnel who hold a security clearance, and this needs to be compensated with additional effective controls such as those listed above. The combination of both personnel security clearances and effective controls provide the most assurance that a cloud consumer’s data will be protected against illegitimate access on behalf of the CSP.
The PSPF provides a mechanism for Australian Government entities to grant temporary access to classified data in some limited circumstances. Temporary access may be provided up to and including SECRET for personnel without a security clearance, after the risks of doing so have been assessed. Temporary access to classified data includes people who are reasonably expected to have only incidental or accidental contact with classified data (e.g. security guards, cleaners, external IT personnel, researchers and visitors such as children who do not have an ability to comprehend the classified data).
The following minimum protections are required to safeguard data accessed on a temporary basis:
- Australian Government entities must limit the duration of access to classified data as follows:
- for short-term access – a maximum of three months in a 12-month period
- for provisional access – until a security clearance is granted or denied
- Australian Government entities must supervise all temporary access. Examples include:
- escorting visitors in premises where classified data is being stored or used
- management oversight of the work of personnel who have the temporary access
- monitoring or audit logging incidents of contact with classified data (e.g. contract conditions that require service providers to report when any of their contractors have had contact with classified data).
NCCEs are required to conduct a risk assessment to determine whether to allow temporary access to classified data.
The Department of Home Affairs recommends the risk assessment include:
- the need for temporary access, including if the role can be performed by a person who already holds the necessary clearance
- confirmation from the authorised vetting agency that the person has no identified security concerns, or a clearance that has been cancelled or denied
- the quantum and classification level of data that could be accessed, and the potential business impact if this data was compromised
- how access to classified data will be supervised, including how access to caveat or sensitive compartmented information will be prevented
- other risk mitigating factors such as pre-engagement screening, entity specific character checks, knowledge of personal history, or having an existing or previous security clearance.
Where an entity intends to grant temporary access to classified data from another entity or third party, the Department of Home Affairs recommends consulting the other entity or party, where appropriate, and obtaining agreement for temporary access to their classified data.
The Department of Home Affairs considers there is merit in obtaining an undertaking (e.g. through a confidentiality or non-disclosure agreement) from the person to protect official data.
Personnel security is just one consideration in the overall assessment and review of a CSP and its cloud services. Personnel security needs to be reviewed by cloud consumers in the context of all other aspects of CSP and its cloud services detailed in this publication and the cloud security assessment report.
All aspects of the CSP’s security needs to be considered when determining if the CSP and its cloud services meet the security requirements and risk tolerance of the cloud consumer.
Physical security
Cloud consumers are responsible for ensuring the physical facilities that contain their data, or are used to access their data, including those owned by third-parties such as CSPs, meet the PSPF physical security requirements. These third-party facilities are most commonly the CSP’s data halls within a data centre, other points of presence, and the CSP’s administrative and support locations from which a cloud consumer’s data can be accessed. Cloud consumers need to ensure these facilities meet the zone requirements defined in the PSPF that are commensurate with the Business Impact Level (BIL) of their data if it was compromised, lost or damaged.
To ascertain if a CSP’s physical facilities that handle a cloud consumer’s data meet the necessary physical security requirements, these facilities can be evaluated by a Security Construction and Equipment Committee (SCEC) Endorsed Security Zone Consultant, or by an NCCE’s Agency Security Adviser (ASA).
A SCEC Endorsed Zone Consultant or ASA can be engaged to evaluate the relevant CSP’s facilities and document all compliances and non-compliances with the PSPF and the Australian Security Intelligence Organisation (ASIO) T4 Technical Notes. The SCEC Endorsed Security Zone Consultant or ASA produces a report that benchmarks the CSP’s facilities against the PSPF and Technical Notes requirements, and details their findings and recommendations.
Cloud consumers whose ASA performs this assessment are recommended to share their report with other cloud consumers who are considering using the CSP. This will prevent other cloud consumers or a SCEC Endorsed Consultants conducting a duplicative assessment.
Before undertaking an assessment of a CSP’s facilities, the CSP needs to map the network and systems in its facilities to identify where its customers’ unencrypted data is stored, processed and communicated. Vulnerable sensitive areas can occur anywhere that data is stored, processed or transmitted in its unencrypted state within the CSP’s infrastructure; whether in a data hall, a meet-me room or a computer operations room.
In addition, where cryptographic operations are performed and key material is stored is an important consideration when determining which vulnerable sensitive areas need to be secured to meet the PSPF security zone requirements.
If the unencrypted data passes outside the security zone, either of the following two options should be implemented:
- Expand the security zone perimeter to include all rooms in which the unencrypted data is stored or transmitted. While this option is simpler to implement, it may pose physical security access restrictions (including security clearance requirements) on some areas, which the CSP may not be able to practicably manage through their business model; or
- Encrypt the data each time it is stored or is transmitted outside the security zone. This option may have significant implications for network infrastructure, including requirements for additional cryptographic ICT hardware and secure rack protection to protect the classified ICT hardware.
A cloud consumer’s chief security officer (CSO) or delegated security adviser must, before consuming a CSP’s cloud services, certify the CSP’s facilities (such as the data halls, administrative and support locations, and points of presence) in accordance with the PSPF and ASIO Technical Notes.
IRAP assessors are required to document in the cloud security assessment report, the physical facilities where a CSP stores, processes, transmits and accesses cloud consumer classified data, and if these facilities have been evaluated by a SCEC Assessor and have an accompanying report and letter. IRAP assessors are also required to address the relevant ISM controls for physical security in their assessment.
ASIO T4 Protective Security Circular 149 – Physical security certification of outsourced ICT facilities (available to cloud consumers on GovTeams) provides additional guidance on PSPF implementation in the outsourced ICT facility or data centre environment, including considering the security risks of using foreign-owned providers and storing data offshore.
For further information on physical security requirements, refer to the PSPF.
For further information on classified data, including BILs, refer to the PSPF.
Cloud service provider locality and ownership
The locality and ownership and control of a CSP need to be considered as part of a cloud consumer’s assessment to determine if the CSP is suitable for handling its data. Foreign-owned CSPs may be subject to extrajudicial control and interference by a foreign entity. This could include a foreign entity compelling a CSP to disclose its customers’ data unbeknownst to its customers. This can include foreign-owned CSPs that provide cloud services in and from Australia.
Cloud consumers also need to consider where the CSP’s administration and support is provided from. Depending on the locations, this can impact personnel pre-employment screening practices, as different countries have different laws about the degree of data that employers can request from their employees.
These aspects of the CSP need to be assessed by cloud consumers considering using its cloud services, to identify any potential risks this presents to the cloud consumers’ systems and data.
Cloud consumers, as part of their review of a CSP, need to consider the following:
- the ownership of the CSP
- the locality of the CSP’s offices, datacentres and administrative and support personnel
- whether the CSP’s personnel are employed by the CSP or a subcontracted
- where its cloud services are provided from
- the potential for any extrajudicial control and interference over a CSP by a foreign entity.
ASD recommends cloud consumers use CSPs and cloud services located in Australia for handling their classified data.
CSPs that are owned, based and solely operated in Australia are more likely to align to Australian standards and legal obligations, and this reduces the risk of any data type being transmitted outside of Australia. These CSPs are also less susceptible to extrajudicial control and interference by a foreign entity.
Foreign-owned CSPs, including those located in Australia, present additional risks that need to be considered as part of the overall risk posture. This includes foreign ownership, foreign interference and extrajudicial control over the CSP’s operations and data holdings. Foreign interference may occur where their own laws, policies or powers allow access to, or control over, the CSP’s operations and data. ASD considers that the involvement of CSPs who are likely to be subject to extrajudicial directions from a foreign government that conflict with Australian law, may risk failure to adequately protect Australian Government data from unauthorised access or interference.
While the locality, ownership and potential for foreign interference are crucial elements to be considered as part of a cloud consumer’s review of a CSP, other elements of the CSP also need to be considered to ascertain a complete understanding of its suitability to handle a cloud consumer’s data. For example, a CSP may be at low risk of foreign interference, but may lack controls in other areas, possibly posing a greater risk than a provider who is not solely operated in Australia, but who has effective controls that meet the security requirements and risk tolerances of the cloud consumer.
Cloud consumers need to consider all aspects of a CSP to make an informed decision about its use and not rely on a single factor to determine a CSP’s suitability.
IRAP assessors as part of their assessment of a CSP are to document in the cloud security assessment report, the ownership of the CSP, the locality of its offices (including support and administrative locations), data centres and the locations its cloud services are provided from.
For further information on securing the cyber supply chain, refer to the Cyber supply chain risk management and Identifying cyber supply chain risks publications.
Information security manual
The purpose of the ISM is to outline a cybersecurity framework that organisations can apply, using their risk management framework, to protect their systems and data from cyberthreats. The ISM also provides a control catalogue with specific controls against which to assess the CSP, its cloud services and an organisation’s own systems.
The ISM is updated on a regular basis to provide up-to-date guidance to mitigate the latest malicious actor tactics, techniques and procedures as observed by ASD. CSPs and IRAP assessors should review the ISM changes and adjust their assessments accordingly to include the latest guidance, or alternatively, make a reference in the assessment report where the updated guidance would have altered the assessment.
Risk management framework
The ISM draws from NIST SP 800-37 Rev. 2, Risk Management Framework for Information Systems and Organizations: A System Life Cycle Approach for Security and Privacy. Within this risk management framework, the identification of security risks and selection of controls can be undertaken using a variety of risk management standards, such as International Organization for Standardization (ISO) 31000:2018, Risk management – Guidelines. Broadly, the risk management framework used by the ISM has six steps:

Cloud controls matrix
To assist CSPs and IRAP assessors with the assessment, the CCM has been developed to provide additional context to the ISM controls for cloud computing. The CCM is used by IRAP assessors to assess the implementation and effectiveness of ISM controls by CSPs for their systems and cloud services.
The CCM provides indicative guidance on the scoping of cloud assessments, and inheritance for systems under a shared responsibility model. The guidance is not definitive, and needs to be interpreted by the IRAP assessor in the context of the assessed system.
Importantly, the CCM also captures the ability of cloud consumers to implement ISM controls for systems built on the CSP’s services, identifying where the cloud consumer is responsible for configuring the cloud service in accordance with the ISM. Information regarding the maintenance of the CCM is addressed within the ‘Maintaining the CSP security fundamentals and cloud services report’ section below.
Cloud security assessment report template
The Cloud security assessment report template is to be used to document the Phase 1 assessment of the CSP and its cloud services. It details the assessment findings that should be included and how it should be presented in the report. This improves the consistency of the cloud security assessment reports, allowing cloud consumers to more easily compare CSPs against one another, and determine which CSP is best suited to their security and business needs.
The Cloud security assessment report template can be customised as needed to best document the findings from the assessment of a CSP and its cloud services. IRAP assessors should, however, limit the changes to the report to only what is necessary, maintaining its structure and headings to ensure reports are consistent.
Applicability of international standards
There are a multitude of international standards and certifications that CSPs can comply with and be certified against. International standards and certifications vary in the level of assurance they provide, and none exist that completely align to the controls in the ISM. For this reason, when assessing a CSP and its cloud services for use by cloud consumers, there is no substitute for a CSP being assessed by an IRAP assessor against the controls in the ISM.
IRAP assessors may, however, use the evidence from other assessments, provided the evidence is applicable, accurate and valid. Given control alignment with other standards is rarely perfect, IRAP assessors should not rely on compliance statements from other standards, but should instead review the supporting evidence and determine whether a control is effective or not.
When reusing evidence from existing certifications or previous assessments, attention must be given to the scope of the certification or assessment. For example, an existing cloud service certification may only be applicable to instances of that cloud service in certain data centres and within certain regions. Similarly, cloud services may consist of a range of integrated cloud service products and a previous assessment of a cloud service may only be applicable to specific products in a particular configuration.
Cloud security shared responsibility
Cloud security is a shared responsibility between the CSP, the cloud consumer and any other third-parties who are involved in providing the complete cloud solution.
As part of using a CSP’s cloud services, cloud consumers need to understand their responsibilities, as well as the responsibilities of the other parties involved in delivering the complete cloud solution. This includes understanding each parties’ responsibilities for securing the cloud, for example, cybersecurity incident response activities, data backups, monitoring, security hardening, patching and encryption. In some of these examples, one party may be entirely responsible, or different aspects may be shared between parties.
As part of the cloud security assessment report, IRAP assessors are to document which party is responsible for securing key aspects of each cloud service in scope of the assessment. This provides cloud consumers with a clear understanding of the different responsibilities each party has for securing the cloud service, including their own.
Regardless of the shared responsibility model, cloud consumers remain accountable for their own data. This includes ensuring the data is appropriately secured, as well as any compromises, losses or damages that occur to the data while using cloud computing.
Third-party cloud solutions
Cloud computing provides an effective way for third-parties to provide their own cloud solutions, such as a Software as a Service (SaaS) provider utilising another CSP’s Infrastructure as a Service (IaaS) to provision their own cloud services. Third-parties are independent of the CSP and are not responsible for the underlying cloud services and infrastructure.
Third-party cloud solutions can increase the assessment difficulty and complexity for IRAP assessors, and make it harder for cloud consumers to identify the risks of its use. This is primarily due to the addition of an extra party who is involved in providing the complete cloud solution. IRAP assessors need to consider both the third-party and its security, plus that of the underlying CSP. Third-parties do not automatically inherit all controls made available to them by the CSP, as third-parties may or may not implement certain controls for their business and operational requirements. Third-parties also rely on their own supply chain, personnel security and secure administration practices to provide their cloud solution. These factors need to be considered by cloud consumers as part of their overall risk assessment.
Similarly, as part of their review of a third-party cloud solution, cloud consumers need to consider the security of the underlying CSP, its cloud services and how it is configured. Ideally, the underlying CSP has been previously assessed by an IRAP assessor and can provide a report. This will allow cloud consumers to better identify the risks of the complete cloud solution, including the underlying CSP and its cloud services.
If an IRAP assessment of the underlying CSP and its cloud services has not been performed, this may make it difficult for cloud consumers to understand the risks of using a third-party cloud solution. Cloud consumers can consider other international standards and certificates as an indication of a CSPs security practices and posture. However, these standards are not a substitute for an IRAP assessment against the ISM.
Cloud data types
There are a variety of data types used in cloud computing, and cloud consumers need to understand what these data types are, where they exist, and how they are handled and secured. Upon understanding the different data types and how they are managed by a CSP, cloud consumers can then make informed decisions about where to store their data that is appropriate to the data’s classification, reducing the risk of it being handled inappropriately.
The most common data types in cloud are:
- Customer data: This is data the cloud consumer creates, generates or uploads to the CSP for storing, processing and sharing using the CSP’s cloud services, this includes the cloud consumer’s authentication details. The cloud consumer, as the data owner, remains accountable for the security of this data type, including any compromises, losses or damages that occur.
- Account data: This is data about the cloud consumer’s account with the CSP and can include billing, contact and usage details.
- Metadata: This includes data about the cloud consumers’ use of the CSP’s cloud services and can include cloud consumer generated data such as resource names, service tag details and utilisation details.
- Support and administrator data: This data type is provided to the CSP’s support personnel and administrators for technical support purposes. This can include logs, monitoring alerts and error reporting details.
The above definitions are to be used as a guide only. Each CSP will likely have their own data type definitions, as well as other data types not covered in this publication. Cloud consumers can refer to the CSP’s cloud security assessment report to identify the data types used by the CSP.
Each CSP’s handling of data often differs per data type, for example, a globally distributed CSP may retain customer data in Australia, but might transmit account data to another country for processing and storing.
It is also common for CSPs to handle the names of customers’ virtual machines, networks and accounts not as customer data, but as metadata. This is often used for analytical purposes and can subsequently be stored in a different location with different controls. In this example, it is advisable for cloud consumers to not place any classified data into fields not treated as customer data due to the risks related to the different handling of the data.
As part of the CSP security fundamentals and cloud services assessment, IRAP assessors need to document the different data types, their definitions, where they are stored, and how they are handled and secured by the CSP.
Cloud assessment methodology
The assessment approach outlined in this publication is a series of qualitative judgements strongly informed by a data-driven quantitative framework, such as that used in the ISM and other cybersecurity frameworks.
Cloud environments can be complex, dynamic, large and unique. These attributes can make it challenging to assess a CSP’s security fundamentals and cloud services to determine if it secure and suitable for handling a cloud consumer’s data. Each assessment is unique and needs to be tailored to the CSP’s particular operating environment and bespoke cloud services.
This publication guides IRAP assessors through an assessment of a CSP and its cloud services to determine its security and residual risks, and to document these findings in the Cloud security assessment report template so that cloud consumers can review and determine if the CSP meets their security requirements and risk tolerances.
Assessment frameworks
While assessments consistent with this publication should always consider the CSP’s operation against the ISM controls, IRAP assessors may also choose to draw in other control frameworks. This provides an opportunity to draw from prior work by the CSP and to supplement any areas where additional, or more comprehensive or insightful coverage can be provided by frameworks other than the ISM.
Sampling principles
All assessments are necessarily abstractions designed to catalogue, quantify and estimate alignment with standards and risk. An assessment of a CSP is influenced by factors including its size, the configuration of its technology stack and the distribution of its operations. Sampling is a logical approach to establishing whether controls are effective across in-scope systems and cloud services. Designing an adequate sampling scheme for an assessment will vary from situation to situation. In designing an approach to sampling, assessors may wish to consider:
- Level of standardisation: Many ICT environments are centrally managed. For example, if checking the validity of configuration on servers which are configured using one technical policy, then potentially one server can be representative of all systems. Also, CSPs often have cloud services that support other cloud services. The built-in security (security that cannot be altered by cloud consumers) of these supportive cloud services can provide a security baseline representative of many cloud services.
- Truly representative: IRAP assessors need to ensure that any points they sample are truly representative, and not a contrived example created only for assessment purposes.
- Different management zones/arrangements: Systems may be operated and administered in different security zones, for different purposes and under different management arrangements. IRAP assessors should consider these differences, and determine if they need to sample data points from across these zones.
- Ease of data collection: IRAP assessors should plan to use and leverage tools as part of their assessment. By driving down the cost of each individual sample, this allows the assessor to more comprehensively gather evidence which will lead to a more accurate assessment.
- Confirmation of unexpected results: IRAP assessors may find they come across results which are inconsistent with their professional experience, such as a CSP demonstrating significant over or underperformance against assessment criteria relative to other similar CSPs. In these situations, IRAP assessors should determine how to take an additional sample/s to confirm the unexpected result.
Scoping principles
Scoping of the cloud security assessment is an important step that helps identify expected authorisation boundaries and the limit of significant dependencies and responsibilities. It also creates abstraction layers that allow systems to be individually identified and described without necessarily having to describe all other related components simultaneously.
Experience with cloud assessments indicates that it is difficult to correctly determine scope at the outset. While IRAP assessors and CSPs should determine an initial scope, this scope should be regularly reviewed to ensure it remains representative of the assessment. In particular, if significant dependencies, potential weaknesses or significant sources of risk are identified which are beyond the initial scope, then the scope should be adjusted.
In addition to any specific agreement between the CSP and the IRAP assessor, the following general scoping principles should be applied:
- the CSP’s control plane should be in scope
- the CSP’s corporate network may be in scope depending on secure administration practices and segmentation and segregation between the corporate network and the CSP’s cloud infrastructure.
Evidence principles
In conducting an assessment of a CSP, IRAP assessors need to gather and review credible evidence to support conclusions on the effectiveness of controls.
In general terms, the evidence of the effectiveness of controls varies from weak evidence, such as a claim that a control exists (e.g. a policy statement), through to strong evidence, such as evidence that a policy is routinely followed or a simulated test which verifies that a technical control performs as expected. More specific guidance on evidence is provided below.
While broad control coverage is important, in performing assessments IRAP assessors should give considerable weight to the quality of evidence about control effectiveness presented to them, or made available to them on request.
Gathering evidence can be time consuming, and IRAP assessors may need to decide on a case by case basis at what point they have sufficient evidence to consider a control effective. IRAP assessors should also consider what evidence can be collected efficiently. For example, verifying that a technical configuration is in place by reviewing the configuration is both a higher standard of evidence, and likely faster and more efficient, than reviewing documentation to try and identify the same thing.
Depending on the size of the assessment, IRAP assessors may need to ensure their assessment team has sufficient skills to efficiently collect, understand and interpret the evidence they will need to review as part of the assessment. See the Expertise Principle below for further information.
Evidence quality
IRAP assessors will find that not all evidence types are covered by these examples, but can still use them as a guide for determining the quality of evidence suitable to assess controls:
- Poor evidence: A policy statement (e.g. repeating the ISM control in an internal document, irrespective of the amount of boilerplate included).
- Fair evidence: Reviewing a copy of the relevant system’s configuration to determine if it should enforce the expected policy.
- Good evidence: Reviewing the technical configuration on the system (through the systems’ interface) to determine if it should enforce the expected policy.
- Excellent evidence: Testing the control with a simulated activity designed to confirm it is in place and effective (e.g. attempting to run an application to check for application control, or attempting to access an external website using a privileged account).
Reusing evidence and inheriting controls
Cloud consumers and CSPs may seek to rely on other ISM based cloud assessments in order to inherit effective controls from those assessments. For example, a CSP who offers SaaS may seek to inherit controls from another CSP’s IaaS.
Acknowledging the inheritance of controls can be an efficient strategy but care needs to be taken to ensure that later assessments do not try and claim controls which do not provide coverage against the full operating context of the later assessment.
Before accepting the inheritance of a control, IRAP assessors need to consider whether the new operating context is fully covered by a control considered in a prior assessment. For example, a SaaS CSP could not claim that the IaaS CSP’s security policy control was entirely inherited – the SaaS CSP will have introduced new risks through the creation of its software, business model and data model that will not have been considered by the IaaS provider when it performed its assessment. However, a SaaS provider might reasonably inherit controls related to the physical protection of equipment and the software isolation mechanism of the virtualisation layer (both of which might be provided by an underlying IaaS CSP). The IRAP assessor, as part of their assessment, needs to determine which controls have been inherited from the underlying CSP, and to what extent they have, or have not been modified.
Identify the authorisation boundary
The authorisation boundary establishes the scope of protection for a system and needs to be clearly defined early in the assessment. The authorisation boundary is what the CSP agrees to protect under its direct management or within scope of its responsibilities. This includes the facilities, people, processes, software and systems that support the CSP’s mission and business function.
All aspects of a CSP, its cloud platform, and any other environments that it is responsible for that interconnect with the cloud platform, are in scope at the commencement of an assessment. Any environments that are deemed out of scope of the assessment are documented in the report and accompanied by a justification by the IRAP assessor for why it has been excluded from the assessment.
Scoping of the CSP’s corporate environments
A CSP’s corporate environment is in the scope of the assessment until it is demonstrated that the corporate environment is sufficiently segregated and segmented from the CSP’s cloud infrastructure and that the CSP performs secure administration practices. This assessment helps determine the risk the CSP’s corporate environment poses to the CSP’s cloud infrastructure. For example, if a CSP’s corporate environment is compromised, the attacker could use this to pivot and gain access to the CSP’s cloud infrastructure, such as their control plane.
The IRAP assessor as part of their assessment needs to determine if the CSP has implemented or met the intent of the Secure Administration and Implementing Network Segmentation and Segregation publications, as well as the associated controls in the ISM. If the IRAP assessor determines that the CSP has not sufficiently mitigated the risk of an attacker pivoting from its corporate environment to its cloud infrastructure, the corporate environment is to be included in the scope of the assessment.
IRAP assessor expertise principle
A cloud environment presents a complex technology stack that can involve multiple parties responsible for the end-to-end solution. This creates a uniquely challenging solution to assess, and necessitates a suitably qualified and skilled assessor, such as an IRAP assessor to perform the assessment.
Depending on the scope of the assessment, it may require more than one individual to adequately perform the assessment. In these cases, IRAP assessors should ensure they are supported by a sufficiently diverse and skilled team to assist with the assessment. CSPs and cloud consumers should enquire as to the cybersecurity and technical depth of the individual or team that will perform an assessment in line with this publication to ensure they have the relevant expertise to perform the assessment.
Cloud assessment steps
The assessment methodology for performing an IRAP assessment of a CSP and its cloud services provides a set of procedures designed to ensure assessments are conducted consistently, thoroughly and aligned to the guidance in this publication and the ISM.
These assessment steps are:
- confirm the intended classification of the data to be handled by the CSP and its cloud services
- identify the authorisation boundary
- confirm the purpose of the assessment, i.e. to be assessed for the purposes of identifying the CSP’s implementation or alignment to the controls defined in the ISM and other relevant Australian Government security policies
- gain an understanding of the CSP, its cloud services and any third-parties that are in scope of the assessment – if any third-parties are involved in providing the cloud solution, such as a SaaS provider using another CSP’s IaaS, has the third-party been assessed by an IRAP assessor, and if not do they need to be
- identify the sources of data, locations, and evidence required to complete the assessment
- identify assessment methods and how data and evidence will be collected and verified
- identify and document the shared security responsibility model for each cloud service in scope
- identify the ISM controls that are in scope of the assessment using the Cloud controls matrix
- identify which party (the CSP, cloud consumer, or any third-parties) are responsible for implementing and maintaining the effectiveness of each ISM control
- obtain evidence of the implementation of ISM controls and their effectiveness – if the CSP has implemented an alternative control, also include how it meets the intent of the control in the ISM
- document any non-implemented or ineffective ISM controls and how the absence of these controls is being risk mitigated by the CSP
- make recommendations to mitigate the risk of absent ISM controls that have not been risk mitigated by the CSP
- document the assessment using the Cloud security assessment report template and the Cloud controls matrix.
Phase 1: CSP security fundamentals and cloud services assessment
Phase 1, the CSP security fundamentals and cloud services assessment, details the processes for assessing a CSP and its cloud services by an IRAP assessor. If required, the IRAP assessor can assess supplementary, new or updated cloud services in Phase 1b. Phase 1 concludes with the review of the CSP security fundamentals and cloud services assessment report by the cloud consumer.
The cloud consumer determines if the CSP and its cloud services meet its security needs and risk tolerance, and if so, approves the CSP and cloud services and progresses to Phase 2.
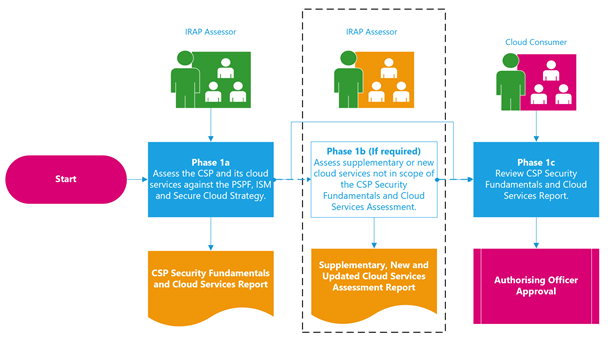
Phase 1a: Assess the CSP and its cloud services
In Phase 1a, the CSP’s security fundamentals and the in-scope cloud services are assessed by an IRAP assessor.
The objective of the CSP’s security fundamentals assessment is to assess and document the security practices and posture of the CSP itself. This is so cloud consumers can determine if the CSP itself is operating securely and producing secure cloud services, and is suitable for handling the cloud consumer’s data.
The other part of the Phase 1a assessment focusses on the CSP’s cloud services that are in scope of the assessment. These cloud services are assessed against the applicable ISM controls, so cloud consumers can determine the security risks of using the CSP’s cloud services.
The IRAP assessor will document the findings, evidence and remediation actions in the Cloud security assessment report template. This report will then be provided to the CSP for sharing with cloud consumers that are considering consuming its cloud services.
CSP security fundamentals assessment criteria
The below criteria are in scope for assessing the security fundamentals of the CSP:
- CSP fundamentals
- governance
- enterprise risk management
- personnel security
- ICT change management
- data type definitions
- data protections
- data deprovisioning and disposal
- supply chain risk management
- vulnerability management
- cybersecurity incident response activities
- secure development lifecycle
- support model
- administrative and support environments
- physical security
- network segmentation and segregation
- system hardening
- secure administration
- cloud infrastructure
- physical security
- network security
- decommissioning hardware
- security operations and monitoring
- cryptography and key management
- data transfers
- identity and access management
- process automation
- continuity and availability.
Cloud services assessment criteria
Below are the assessment criteria for cloud services, applied to each cloud service in scope of the assessment. Common controls and implementations can be reused where applicable:
- description
- cloud service locality
- cloud service shared responsibility model
- cloud service architecture diagram
- components and dependencies
- inbound and outbound interfaces
- protection of data at rest
- data backup and restore
- data portability
- tenancy segmentation and segregation
- cloud service security visibility
- security baseline
- deviations from baseline
- customer responsibilities & implementation guidance.
Phase 1a: Reassessment timeframe
A CSP and its cloud services are reassessed at least once every 24 months. The focus of the reassessment is the security-related changes that have occurred to the CSP and its cloud services since the last assessment, as well as new inclusions such as new cloud services. Any addendums added by the CSP to its previous cloud security assessment report are to be independently verified in the reassessment and included in the new report.
Between assessments, CSPs are to keep their customers informed of changes to their security fundamentals and cloud services that impact their security baseline and that of its customers’ systems. This continual disclosure to the CSP’s customers is primarily to be achieved by updating the cloud security assessment report with addendums as soon as is reasonable to do so. Any new addendums added to the report are to be communicated with the CSP’s customers who have used the report as part of their assessment of the CSP.
For those aspects of the CSP and its cloud services where there has been no change, or only insignificant changes that have not impacted the CSP’s security baseline, the evidence used in previous assessments can be reused to validate controls. However, IRAP assessors are to consider the age of the evidence being supplied and determine if the evidence is still valid and accurate.
Although CSPs are to be assessed at least once every 24 months, assessment reports that are older than 24 months are not automatically invalidated by this timeframe. As reports age, the likelihood of them being inaccurate and invalid increases. They may, however, still be relevant depending on the CSP’s change cadence. Cloud consumers need to check with the CSP on the validity and currency of the report if it has not been recently completed. Due to the rapid nature of change in cloud computing, it is likely a CSP’s systems and cloud services have changed, even within a short period of time. CSPs can support cloud consumers by updating their reports with addendums, document and detailing any changes to their systems and cloud services that have occurred post the original report.
Between assessments, certain events may require a reassessment to revalidate the security of a CSP and its cloud services. A sample of these events is listed below; however, any event that significantly affects the security of the CSP or its cloud services may require a reassessment:
- changes to security policies relating to the CSP, its cloud platform or its clouds services
- detection of new or emerging cyberthreats to the CSP, its cloud platform or its cloud services
- the discovery that controls for the CSP, its cloud platform or any of its cloud services are not as effective as intended
- a major cybersecurity incident that affects the CSP
- changes to the ownership of the CSP
- new, or changes to existing, extrajudicial laws that apply to the CSP
- changes to the location of where customer data is stored
- major architectural changes to the CSP, its cloud platform or its cloud services.
Phase 1b: Supplementary, new and updated cloud services assessment
A Phase 1b assessment is only required to be performed when a cloud consumer wants to use a CSP’s cloud service or services, and the cloud service or services have not previously been assessed. Examples of why a Phase 1b assessment could be required are:
- the cloud service or services were not in scope of the CSP’s cloud security assessment report
- the CSP has released a new cloud service or services post the completion of its cloud security assessment report
- the CSP has made significant changes to a cloud service or services that impacts the security documented in the cloud security assessment report.
Phase 1b cloud service assessments are performed by an IRAP assessor. These assessments can be performed independently of the Phase 1a assessments and between reassessments, alleviating the need for cloud consumers to wait for a Phase 1a reassessment to occur, and allowing them to quickly use a CSP’s cloud services. A Phase 1a assessment is required to be completed before a Phase 1b assessment can occur, as cloud consumers need to review a Phase 1b report (referred to as a supplementary, new and updated cloud services report) in combination with the Phase 1a cloud security assessment report.
These assessments are documented in the cloud security assessment report, omitting the Introduction and CSP Security Fundamentals Assessment sections from the report.
Phase 1c: Review cloud security assessment report
In Phase 1c, the cloud consumer reviews the cloud security assessment report and if required, the supplementary, new or updated cloud services report, and determines if the CSP and its cloud services meet the cloud consumer’s security requirements and risk tolerance. The cloud consumer’s authorising officer or delegate can approve the use of a CSP and its cloud services on behalf of the cloud consumer. This approval may be caveated that the CSP and its cloud services are used in a predefined configuration, for example only certain services or regions are permitted to be used by the cloud consumer. These specific configurations are documented and form part of the approval evidence generated by the authorising officer or their delegate.
Phase 2: Cloud consumer systems assessment and authorisation
The majority of cybersecurity compromises involving cloud computing are due to cloud consumers failing to implement the necessary controls for those aspects of the cloud environment they are responsible for under the shared responsibility model. Because of this, cloud consumers need to ensure they understand their responsibilities for securing their own cloud systems, and implement the necessary controls to mitigate the risk of a cyber-attack to an acceptable level. To ensure the cloud consumer’s own cloud systems have achieved the desired security baseline, these systems also need to be assessed to gain assurance the completed cloud solution, including the CSP and its cloud services, as well as the cloud consumer’s systems meet the security requirements and risk tolerance of the cloud consumer.
The Phase 2a assessment provides additional guidance for assessing and authorising the cloud consumer’s own cloud systems. This assessment is performed by an IRAP assessor. Phase 2 concludes with the review by the cloud consumer’s authorising officer or their delegate of the Cloud Authorisation Package, which includes the CSP’s cloud security assessment report, and if applicable, any supplementary, new or updated cloud services report, and the cloud consumer cloud systems report. The authorising officer provides the authority to operate based on the acceptance of security risks associated with the operation of the entire cloud solution.
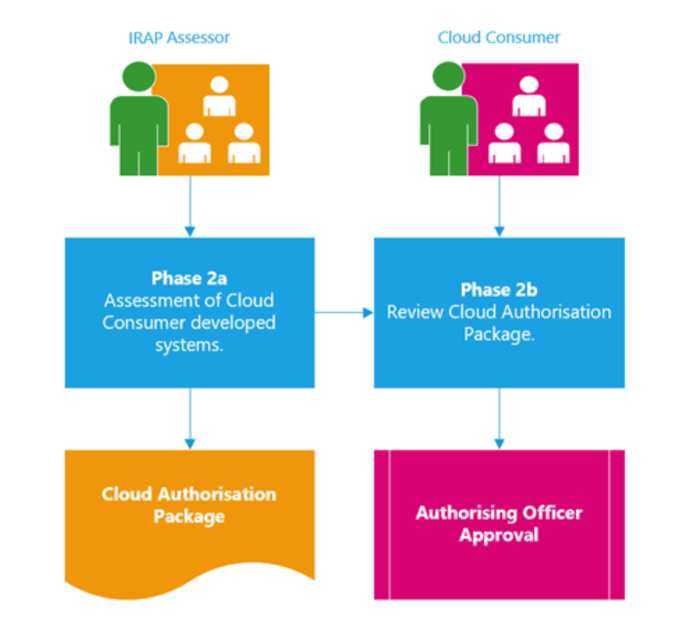
Phase 2a: Assessment of cloud consumer developed systems
Cloud systems developed or configured by cloud consumers need to be assessed to ensure they meet the cloud consumer’s security requirements and risk tolerance. These cloud consumer systems include any systems developed or configured by the cloud consumer that leverages the CSP’s cloud services, for example hosting a website or the configuration of a SaaS-based collaboration platform. It is important these systems do not lower the security baseline provided by the CSP and introduce new weaknesses.
The guidance in this publication, the Cloud controls matrix, the ISM and other relevant guidance from ASD should be used in the assessment of a cloud consumer’s own systems. As part of this assessment, cloud consumers need to identify which controls from the CSP and its cloud services have, and have not been inherited. Where controls have not been inherited, cloud consumers need to consider the risk, and determine if any compensating controls are required. This will enable cloud consumers to select the controls that are applicable and need to be implemented for their cloud-based systems as part of the risk management framework detailed in this publication. These controls can then be assessed for their effectiveness to determine if other controls are required, and if the cloud consumer’s systems meet their security needs and risk tolerance.
The assessment of cloud consumer systems needs to be conducted during all phases of the system development lifecycle, ensuring any security issues are identified and remedied early on. It is common for cloud systems to be continuously developed throughout their lifecycle, rather than remaining static. As such, point-in-time assessments are of limited value, and an iterative approach to assessing and validating these systems is necessary. Agile and DevSecOps practices are encouraged for the development and security of cloud consumer systems to perform this iterative approach to development and security.
The shared responsibility model for each cloud service should also be reviewed and updated as necessary. Depending on the configuration of a cloud consumer’s systems, this could alter the original shared responsibility model documented in the cloud security assessment report, resulting in responsibilities transferring between the CSP and the cloud consumer.
The Phase 2a findings are documented in the Cloud Authorisation Package and reviewed by the cloud consumer’s authorising officer.
Phase 2b: Review cloud authorisation package
Before the cloud environment can be granted authorisation to operate, sufficient information should be provided to the authorising officer or their delegate to help them to make an informed risk-based decision on whether the security risks associated with its operation are acceptable or not. This information should take the form of an authorisation package that includes:
- the CSP’s cloud security assessment report
- any supplementary, new or updated cloud services report (if required)
- the cloud consumer cloud systems report.
The authorising officer or their delegate reviews the Cloud Authorisation Package and determines if the cloud environment, comprising the CSP, its cloud services and the cloud consumer’s systems meet their security requirements and does not exceed their risk tolerances. In some cases, the security risks associated with a system’s operation will be acceptable and it will be granted authorisation to operate; however, in other cases the security risks associated with operation of a system may be unacceptable. In such cases, the authorising officer may request further work, and potentially another security assessment to be performed. In the intervening time, the authorising officer may choose to grant authorisation to operate but with constraints placed on the system’s use.
Finally, if the authorising officer deems the security risks to be unacceptable regardless of any potential constraints on the system’s use, they may deny authorisation to operate until such time that sufficient remediation actions, if possible, have been completed to an acceptable standard.
All Phases: Continuous monitoring and assurance
Continuous monitoring and assurance provides ongoing awareness of evolving security risks, vulnerabilities, threats, controls and incidents to provide assurance of a system’s security posture. This is a responsibility shared between the CSP and cloud consumer.

Ongoing awareness of evolving cybersecurity risks, vulnerabilities, threats, controls and incidents, coupled with performing ongoing security assessments of these changes, determines whether the set of deployed controls in a cloud system remains effective over time. The ongoing assessment of controls results in greater control over the security posture of the system and enables informed risk-management decisions in a timely manner.
Activities to support continuous monitoring of the threat environment, security risks and controls associated with a system, will differ from system to system, but it is important to consider the dependencies of the system, including software and other cloud services.
From time to time, ASD will release publications and advisories to assist CSPs and cloud consumers with identifying and mitigating security risks. While there is no requirement for CSPs and cloud consumers to be immediately compliant with every update to the ISM, timely processing of ISM changes is recommended to assist with ongoing identification of risks. ASD security advisories are released in response to current and active threats it is aware of. These advisories are usually more time sensitive and affected entities are recommended to review and implement the advice in a timely manner.
Measures to proactively monitor and manage vulnerabilities in systems can provide CSPs and cloud consumers with a wealth of valuable information about their exposure to cyberthreats, as well as assist them to determine security risks associated with the operation of their systems. Intentional changes between different releases or ongoing improvements should also be considered for their impacts on the security risks of a system.
CSP systems
The CSP is responsible for monitoring and assuring the security of its systems and related hardware, software and facilities. Security-related information determined through continuous monitoring, where relevant to cloud consumers, can be included in the addendums to the CSP’s cloud security assessment report, and used to issue CSP security advisories as appropriate.
Additionally, CSPs are in a unique position to proactively undertake automated activities to identify and report on possible cloud consumer misconfigurations that do not align with security best practices. CSPs have some visibility across all their cloud consumers (including access that cloud consumers do not have), they have the best knowledge of their platforms and are best placed to provide these unique insights. Security best practices can include both the CSP’s general best practices and best practices for aligning with the ISM on the CSP’s cloud platform. CSPs are encouraged to provide configuration guidance to its cloud consumers to assist them to develop secure systems on their cloud services.
CSPs may also wish to provide a configuration option that proactively prevents the deployment of resources against security best practices, enabling security by default.
Cloud consumer systems
Maintaining oversight of the risks associated with using a CSP and its cloud services is important, as CSPs and their cloud services are in a constant state of change and the associated risks are rapidly evolving. Cloud consumers should develop a continuous monitoring and assurance plan that includes detailing how they will monitor the CSP and its cloud services to identify and respond to any changes that could impact the cloud consumer’s systems and data. This should include the processing of CSP’s security advisories and how it relates to their ongoing authorisation processes. Typically, this is integrated with their time-driven and event-driven authorisation processes to maintain ongoing authorisation, whereby the cloud consumer’s authorising officer is provided with the necessary information regarding the security state of the system to determine whether the mission or business risk of continued system operation is continuously acceptable.
Cloud consumers need to continually monitor their own systems and data hosted in the cloud. Often, CSPs have limited visibility of the customer’s usage of their cloud platform and this will not include the context of the cloud consumer’s systems, use case and data. Therefore, CSPs can only have limited responsibilities for monitoring a cloud consumer’s systems and data for any cybersecurity compromises. It is therefore important for cloud consumers to develop and maintain their own processes for monitoring of their cloud systems as part of their wider operational security responsibilities. Some CSPs provide a cloud service that assists cloud consumers to monitor their own systems and data. cloud consumers should review the security related features of CSP services, as well as potential alternative solutions, to identify the capabilities the cloud consumer needs to provide effective continuous monitoring.
Maintaining the CSP security fundamentals and cloud services report
The IRAP assessor provides the final cloud security assessment report to the CSP who is responsible for maintaining the accuracy and currency of the report between independent assessments by adding addendums to the report. CSP addendums:
- are self-assessed separate documents that in no way modify the contents of the independent cloud security assessment report in order to preserve authenticity
- are informed by the CSP’s continuous monitoring and assurance activities
- detail any changes, deviations, corrections and clarifications required to maintain the accuracy and currency of the report, including the Cloud controls matrix
- detail any changes resulting in either improvements or deficiencies/weaknesses
- uphold the current version’s structure
- act as a trigger for a consumer security advisory.
While addendums will initially not be independently verified, they will prevent the report from becoming inaccurate or invalid as the CSP and its cloud services evolve over time. Any information contained in the addendum is to be independently verified the next time the CSP and its cloud service undergo an independent assessment. Additionally, CSPs are recommended to issue addendums covering any significant changes to the Cloud security assessment report template published by ASD.
CSPs with previous IRAP assessments issued before the Cloud security assessment report template was available, may undertake a self-assessment addendum to the report using the structure of the new template to enable transition and closer alignment with the updated process. Noting that cloud consumers should consider the age of the report.
CSP security advisories
CSPs should provide a mechanism to inform cloud consumers of applicable security events that may impact the security and risk of the cloud consumer’s own systems and data. Ideally this mechanism should include a programmatic interface to enable automation and integration with the cloud consumer’s existing Security Information and Event Management (SIEM) or process systems. This can include weaknesses or positive impacts, such as the release of a new security feature that provides further protection for a cloud consumer’s cloud systems.
At a minimum, applicable security events should include:
- publication of any addendums to the CSP security fundamentals and cloud services report
- planned changes that will significantly affect the security posture of the system, including supply chain changes
- the discovery that controls for the CSP, its cloud platform or any of its cloud services are not as effective as intended
- security incidents or discovered vulnerabilities that either affect the cloud consumer or cannot be ruled out as affecting the customer – this includes the identification of misconfigurations, data spills, cybersecurity intrusions and customer data access by the CSP
- decisions to delay or not undertake a change, including those from upstream vendor updates or security advisories
- any event that significantly affects the security of the CSP or its cloud services that otherwise may trigger a reassessment.
The security advisories should include (as appropriate):
- security impact analysis covering:
- specific weaknesses or deficiencies in deployed controls and the source of the identified weaknesses
- severity of the identified control weaknesses or deficiencies
- scope or affected assets of the weakness in components within the environment
- proposed risk mitigation approach to address the identified weaknesses or deficiencies in the control implementations (for example, prioritisation of risk mitigation actions and allocation of risk mitigation resources).
- any related CSP security fundamentals and cloud services report addendums.
Continually disclosing information to cloud consumers will enable them to make timely, risk-informed decisions about the operation of their systems and the protection of data, them to efficiently identify and respond to any risks deemed unacceptable.
Continuous disclosure contract provisions
Cloud consumers, as part of their contract with a CSP, should stipulate a requirement for the CSP to continually disclose any applicable security events via advisories to their cloud consumers.
Further information
The Information security manual is a cybersecurity framework that organisations can apply to protect their systems and data from cyberthreats. The advice in the Strategies to mitigate cybersecurity incidents, along with its Essential Eight, complements this framework.
Contact details
If you have any questions regarding this guidance you can write to us or call us on 1300 CYBER1 (1300 292 371).
